October is National Cybersecurity Awareness Month
Since 2004, the President of the United States and Congress have declared October to be Cybersecurity Awareness Month, helping individuals protect themselves online as threats to technology and confidential data become more commonplace. The Cybersecurity and Infrastructure Security Agency (CISA) and the National Cybersecurity Alliance (NCA) lead a collaborative effort between government and industry to raise cybersecurity awareness nationally and internationally.
See Yourself in Cyber
This year’s theme – “See Yourself in Cyber” – emphasizes that while cybersecurity may seem like a complex subject, ultimately, it’s all about people. This October will focus on the “people” part of cybersecurity, providing information and resources to help educate CISA partners and the public and ensure all individuals and organizations make smart decisions whether on the job, at home, or at school – now and in the future.
4 Things You Can Do
Throughout October, CISA and NCA will highlight key action steps that everyone should take:
- Enable Multi-Factor Authentication
- Use Strong Passwords
- Recognize and Report Phishing
- Update Your Software
YYTECH has a catalog of cybersecurity articles that can also be shared, and remember that YYTECH can help ensure your data is protected.
Cybercrime is real, and it’s increasing …
According to the Verizon Business 2022 Data Breach Investigations Report (2022 DBIR), 25% of total breaches in the 2022 report resulted from social engineering attacks. When you add human errors and misuse of privilege, the human element accounts for 82% of analyzed breaches over the past year.
The latest data from Dark Reading’s annual Strategic Security Survey shows that phishing is an organization’s biggest problem, with 53% of organizations citing phishing as the cause of a security breach.
According to the IBM 2022 Cost of a Data Breach report, the average cost of a data breach in 2022 is $4.35 million.
YYTECH can help protect your organization with these preventive services:
YeoSecure is 24/7/365 security monitoring of networks and is designed to prevent and accelerate the detection of cybersecurity threats.
Security Awareness Training showcases best practices for a company’s first line of defense – its employees – and teaches them the dangers of online threats.
As always, remember to be aware and think before you click!
As our reliance on technology grows, the risk of individual and commercial cyberattacks increases as well. Hackers now have more opportunities to steal sensitive data than ever before. We’ve created this Cybersecurity eBook to share insights and tips so you can better understand modern cyber risks and the potential impact they could have on your organization. In the eBook, we discuss:
- What types of cyberattacks to watch for, how they work, and emerging trends you need to be aware of.
- How to assess your cybersecurity risks, from taking inventory of the devices on your network to evaluating the impact an attack would have.
- What to do if a breach occurs, from contacting your cybersecurity insurance provider to conducting a thorough analysis of public sites to ensure no private information was posted accidentally.
- How to protect your organization from cyberattacks and the protections you can implement today to decrease your risk.
This 20-page eBook is a comprehensive guide to cybersecurity. We hope you find it useful as you analyze how to keep your organization safe in the digital world.
How can I avoid being phished?
The best thing is to treat every email with caution. If you’re unsure, check the address it has been sent from, look for grammatical errors, and see if the layout looks like a regular email from that person or company. If you’re unsure, don’t click any link.
What’s an insider threat?
It’s the name for when someone within your business gives cybercriminals access to your devices or network. Usually, it’s not malicious. But it’s why regularly training your team in cybersecurity is a must.
How do I choose the right backup for my data?
Security and reliability should be your primary considerations. Get in touch, and we’ll tell you what we recommend.
Information used in this article was provided by our partners at MSP Marketing Edge.
New insight into what happens during and after a ransomware attack paints a rather dismal picture of what to expect. According to Cybereason’s Ransomware: The True Cost to Business report, the reality of mid-and post-ransomware attack circumstances is anything but resilient.
According to the report, 73% of all organizations have experienced a ransomware attack in the last 12 months. And of those that were attacked, the question of whether the ransom was paid always comes up:
- 41% paid to “expedite recovery.”
- 28% paid to “avoid downtime.”
- 49% paid to “avoid a loss in revenue.”
But even after paying the ransom, 80% experienced a second attack, and 68% were asked for a higher ransom!
Then there is the aftermath to the organization:
- 54% still had corrupted systems or data
- 37% had to lay off employees
- 35% had a C-level resignation
- 33% had to suspend business temporarily
What’s interesting is that 75% of organizations believe they have the right contingency plans to manage a ransomware attack – a number that hasn’t changed in the last year, according to Cybereason.
While your organization “has a plan” to address ransomware, the only truly effective plan is to attempt to stop it all. This strategy needs to include empowering your users with Security Awareness Training so they can distinguish between legitimate email and web content from malicious content intent on kicking off a ransomware attack.
Information in this article was provided by our partners at KnowBe4.
Cybersecurity culture is a hot topic among many organizations and security professionals. But what are organizations doing to build a strong security culture?
To help shed some light on the topic, KnowBe4 asked attendees at Infosecurity Europe 2022 for their views. Of the 179 participants, 41.3% were from large enterprises, and 64% stated they were in a security or IT position, including CISOs and Heads of Security.
Where are efforts focused?
Participants were asked where they were focusing efforts to build a security culture, with most directing efforts into security awareness training (84.5%) and communicating values and expectations from employees regarding security (84.5%).
More than one-quarter (27.2%) do not put much effort into measuring employees’ understanding of security. This begs the question: Are most organizations still caught up in the compliance mindset of delivering training and not being interested in measuring whether employees fully understand the implications of their actions?
Factors driving security culture
According to the survey results, the threat of cyberwarfare (30.2%) and experiencing a data breach or cyberattack (30.2%) are the most significant influences for wanting to improve security culture. Cyberwarfare has undoubtedly been influenced in recent months by the ongoing war in Ukraine and the associated cyberattacks that have taken place.
Witnessing other organizations in the same industry suffer a cyberattack was also a significant driver (29.1%).
While getting a push to improve security culture from external events or sources is always positive, all the goodwill in the world will not impact the culture unless it is through effective communication channels.
How to improve your organization’s cybersecurity culture
Having security awareness advocates is the most effective way of communicating security awareness messages (27.9%), with gamification ranking second (24.6%).
These are not surprising. As the adage goes, people buy from people they trust. This is why security advocates are considered so effective and essential to any organization’s strategy to improve its security culture.
Gamification tends to be popular because of the level of engagement it brings. Furthermore, it reinforces the message that information needs to be delivered in an engaging and consistent manner to ensure the lessons are taken on board.
Is a strong culture worth it?
It appears as if many organizations are keen to build a strong security culture. But is this a case of keeping up with the Joneses, or is there a real benefit to building a strong culture?
The vast majority (92.9%) said that it is very or somewhat likely that having a solid security culture can reduce the risk of security incidents.
Ultimately, reducing the risk of security incidents is the objective of cybersecurity, whether through technical controls, procedures, or educating colleagues.
While the focus for many years has been on the technology side of security, we cannot neglect the human factor. By working on building a strong security culture, organizations can ensure they are doing the best they can to minimize the risk of security incidents to their organization.
Information in this article was provided by our partners at KnowBe4.
As threat actors look for ways to evade detection by security solutions, the use of cloud applications has seen a material jump in the last 12 months, according to new data.
While we see plenty of cyberattacks that utilize dark infrastructure to accomplish malicious activities, threat actors are using the legitimacy of web-based application platforms to ensure phishing email delivery to the inbox.
In the latest report from Palo Alto Network’s Unit42, Legitimate SaaS Platforms Being Used to Host Phishing Attacks, we find that the increases are far more significant than expected. According to the report, the following types of SaaS platforms were included in their analysis of phishing URLs:
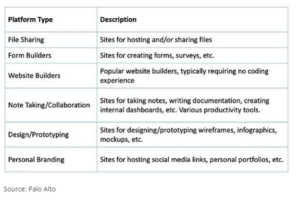
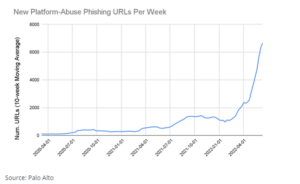
They found a staggering and continually increasing trend of misuse of these platforms to host phishing URLs. In the 12 months between June 2021 and June 2022, the number of malicious phishing URLs increased by 1,100%.
According to the report, these sites were used for many purposes, including:
- Design / Prototyping
- Website Building
- Form Building
The result is that malicious websites that look like legitimate brands are being used for attacks focusing on both credential theft and fraud.
And, given the “hockey stick” chart above, organizations should expect this to continue, making it more challenging to spot phishing emails via security solutions. This makes it necessary to employ users to play a role in identifying and stopping phishing emails – something they’ll need to be educated on via Security Awareness Training to do it effectively.
Information used in this article was provided by our partners at KnowBe4.
It’s only natural to want to know what’s happening around you. And it’s the same with supply chains in your business. Knowing that things are running smoothly, and seeing what’s happening, puts your mind at ease.
But a recent report from the Economist Intelligence Unit (EIU) says that more than half of companies lack end-to-end visibility in their supply chains, making them vulnerable to unexpected risks.
It’s not just about seeing what’s going on around your business. Having a clearer picture of your supply chain and where your products come from also dramatically impacts your bottom line. As well as your reputation within your industry.
- Research has shown that customers are willing to spend up to 10% more on products when they know where they’ve come from. As well as what materials and ingredients were used and where they were sourced.
- More and more companies are being asked to be open and share information about their supply chains. Not having that information on hand can seriously impact your reputation and play into the hands of your competitors who do.
- With hybrid and remote working on the increase, your teams need to access supply chain data from various locations on various devices. Not being able to offer them this option can mean them missing out on additional sales.
- CFOs are under constant pressure to manage costs and productivity. But it’s harder to make smart business decisions when you don’t have the data or insights into what’s happening.
The right business management tool gives you complete visibility across your entire supply chain. Everyone—from suppliers to customers—can easily see everything they need to know and more, whether it’s customer information, stock levels, past purchases or quotes.
Sage consolidates your work systems into one solution, allowing for better collaboration for in-office and remote teams. It also reduces repetitive tasks through automation, saving your staff time and improving efficiency. Want to learn more? Contact Yeo & Yeo Technology today.
Information used in this article was provided by our partners at Sage.
Blacklisting is where you block something you don’t trust. It keeps networks and devices safe from harmful software and cybercriminals. But there’s another, safer way of doing that – and that’s called whitelisting.
Rather than trying to spot and block threats, you assume everyone and everything is a threat unless they’ve been whitelisted.
But what is the right approach to keeping your business data safe? This debate rages on, with many IT professionals holding different views.
Here are the main differences…
- Blacklisting blocks access to suspicious or malicious entities. Whitelisting allows access only to approved entities.
- Blacklisting’s default is to allow access. Whitelisting’s default is to block access.
- Blacklisting is threat-centric. Whitelisting is trust-centric.
There are pros and cons to each approach. While blacklisting is a simple, low-maintenance approach, it will never be comprehensive as new threats emerge daily. It’s easy to miss a threat, as cybercriminals design software to evade blacklist tools.
Whitelisting takes a stricter approach and therefore comes with a lower access risk. But it’s more complex to implement and needs more input. It’s also more restrictive for people using the network and devices.
Controlling access is at the center of network security. Blacklisting and whitelisting are both legitimate approaches to managing access to your networks and keeping your data secure. The right one for you depends on your organization’s needs and goals. If you’d like to discuss which approach is best for your business, get in touch.
Information used in this article was provided by our partners at MSP Marketing Edge.
Cyberattacks via SMS messaging are on the rise and are having such an impact the Federal Communications Commission has released an advisory on Robotext phishing attacks (or smishing).
According to Verizon’s 2022 Mobile Threat Index, 45% of organizations have suffered a mobile compromise in 2022 – that’s double the percentage of organizations in 2021. If you’re wondering if it’s purely a shift in tactics on the cybercriminal’s part, think again. According to Verizon:
- 58% of organizations have more users using mobile devices than in the prior 12 months
- Mobile users in 59% of organizations are doing more today with their mobile devices than in the last 12 months
- Users using mobile devices in 53% of organizations have access to more sensitive data than a year ago
And keep in mind that while there are plenty of security solutions designed to secure mobile endpoints, we’re talking about personal devices that are used as a mix of corporate and personal life. This makes for a very unprotected target by cybercriminals.
So, it shouldn’t be surprising that the FCC has issued an advisory warning about the increased use of robotexting-based phishing scams targeting mobile users, commonly called ‘smishing.’
Some of their warning signs include:
- Unknown numbers
- Misleading information
- Misspellings to avoid blocking/filtering tools
- 10-digit or longer phone numbers
- Mysterious links
- Sales pitches
- Incomplete information
We’ve seen smishing scams impersonating T-Mobile, major airlines, and even the U.K. Government. So consumers and corporate users alike need to be aware of the dangers of text-based phishing attacks – something reinforced through continual Security Awareness Training.
Information used in this article was provided by our partners at KnowBe4.
First, the term “stack” is used because it describes layers that deliver services and exchange information to achieve a higher-level service. The concept of a “security stack” communicates that security must be an integrated set of services.
Every layer is a particular technology with its own features. The security stack needs to be designed from the ground up, knowing that security is a vital network element, just like multiple blueprints (electrical, plumbing, flooring, etc.) are required to construct a safe and stable building.
So, what would be a bare-minimum security stack?
- Email security: Protection from email-borne threats
- Firewalls: A barrier between a trusted and untrusted network
- Anti-virus: Protection for endpoints in the business
- DNS Filtering: software that blocks threats before they reach your network
In addition to these bare-minimum security tools, we recommend:
- Security Awareness Training to educate and build your human firewall
- Multi-factor authentication to verify a user’s identity
- Patching and vulnerability management to decrease vulnerabilities
 That said, many other layers (tools) should be added to protect your organization. Below is a picture of a security stack that a managed security service provider (MSP), like Yeo & Yeo Technology, can create for their clients. The layers together provide a higher-level service and include some of the bare minimum listed above.
That said, many other layers (tools) should be added to protect your organization. Below is a picture of a security stack that a managed security service provider (MSP), like Yeo & Yeo Technology, can create for their clients. The layers together provide a higher-level service and include some of the bare minimum listed above.
Are you interested in building a comprehensive security stack for your business? Contact us today.
Information used in this article was provided by our partners at KnowBe4.
When the concept of cyber insurance was first introduced, it seemed like a shakedown and another way for insurers to take an organization’s money. But today, according to Sophos’ Cyber Insurance 2022: Reality from the Infosec Frontline report, cyber insurance policies are now held by 94% of organizations.
So, what’s driving this adoption of cyber insurance?
Much of the adoption lies in organizations experiencing an attack and realizing they need insurance to cover what their own cybersecurity stance doesn’t. According to the report:
- 57% of respondents experienced an increase in the volume of cyberattacks on their organization
- 59% saw the complexity of these attacks increase
- 53% said the impact of these attacks had also increased
- 89% of those hit by ransomware have cyber insurance against ransomware
And it’s getting more challenging to obtain cyber insurance as insurers evolve their minimum cybersecurity standards. According to the report:
- 94% of those with cyber insurance said the process for securing coverage had changed over the last year
- 54% say the level of cybersecurity they need to qualify for insurance is now higher
- 47% say policies are now more complex
- 40% say fewer companies offer cyber insurance
- 37% say the process takes longer
And even if you get a policy, there’s no guarantee the attack scenario you encounter is covered, as many organizations have needed to go to court over being paid out based on their policy.
So, the best plan is to have as secure an environment as possible – including securing your users with continual Security Awareness Training to minimize the threat of email- and web-based social engineering attacks designed to give attackers entrance into the organization’s network.
Information used in this article was provided by our partners at KnowBe4.
Fresh data on data breach costs from IBM show phishing, business email compromise, and stolen credentials take the longest to identify and contain.
There are tangible repercussions of allowing your organization to succumb to a data breach that starts with phishing, social engineering, business email compromise, or stolen credentials – according to IBM’s just-released 2022 Cost of a Data Breach report.
According to the IBM report, the average cost of a data breach in 2022 is $4.35 million, with an average of 277 days to identify and contain the breach. The following are the average data breach costs based on the initial attack vector:
- Phishing – $4.91 million
- Business Email Compromise – $4.89 million
- Stolen Credentials – $4.50 million
- Social Engineering – $4.10 million
Why so much? A lot of it has to do with how long threat actors act undetected as they move laterally within your environment, gain access to credentials and data, and exfiltrate your valuable data.
According to the report, the longest times are attributed to attacks that involve your users:
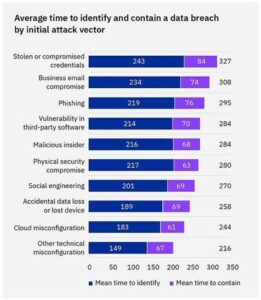
Source: IBM
With the average number of days to detection and containment being 277, it’s evident that stolen credentials, phishing, and business email compromise (the attack vectors your users play a role in!) push those numbers up, giving attackers an additional 1-2 months to continue their malicious activities.
Additional takeaways
- Employee security awareness training can cover 49% of the breach types
- Employee training saves $247K in terms of data breach impact cost
- Breaches in the public cloud are costliest for the organizations that don’t invest in employee training and expect public cloud providers to take care of breaches.
We already know that phishing and BEC attacks focus on either stealing credentials or infecting endpoints, putting the user receiving the malicious email, phone call, text, etc., squarely in the middle of the discussion that results in these massive data breach costs.
Users need to play a role in your security strategy to help mitigate the risk of successful attacks. Security Awareness Training can teach your users how to identify suspicious content in email and on the web, helping to avoid any interaction that could result in a data breach.
Information in this article was provided by our partners at KnowBe4.
Payroll is one of the most commonly underused resources available to businesses when it comes to insight. It has the power to shine a light on your largest resource and overhead—your people. Tapping into payroll data analytics can help you better understand where your strengths and weaknesses lie. A good payroll system should provide data showing where your money is going and how you can benefit from your most valuable assets, your employees and customers.
In the past, the unfortunate perception of payroll was of a repetitive administration machine. But that’s changing. Innovative updates to payroll technology have given payroll a seat at the reporting table, and businesses can better analyze their greatest asset and largest cost.
Payroll now has room to play a more strategic and valuable role. Employee compensation is not simply a cost to contain but an important consideration that will save money and drive efficiency in the long term.
However, payroll professionals must use and understand the large amounts of data available to them if their businesses are to keep up with the competition. Research by Sage and IDG has found that companies with more effective data grow 35% faster.
Reporting is crucial
As highlighted by our research, reporting is key to business success. It can contribute not only to growth but also to the productivity of employees. Businesses with more usable data increase productivity by 10%.
For payroll professionals, it allows you to understand and make the best use of your company’s biggest capital investment—the employees. After all, the wages a business commits to the workforce directly impact the money it makes.
Reporting and analytics are of immense value. And they can help in the two biggest financial priorities—cost reduction and forecasting—allowing your company to grow and succeed in a business world where every advantage counts. Combining payroll data with qualitative elements such as performance culture, skills, behavior, and experience can help you form a picture of the issues affecting business performance.
Information used in this article was provided by our partners at Sage.
I think I’ve clicked an unsafe link. What should I do?
The faster you act, the less damage or data loss you’ll have. Get in touch with your IT support partner immediately. It’s always a good idea to have a response and recovery strategy in place for when this happens.
My external drive isn’t showing up when connected
First, make sure it’s powered up! Then try it in a different USB port or another device. This will let you know if the drive or your device is the issue. You may need to enable it in Windows manually.
What’s the best antivirus software for my business?
Not all antivirus software is equal, and the best solution for your business may be completely different than it would be for the company next door. It depends on your infrastructure. We’d love to help with a recommendation, so get in touch.
Information used in this article was provided by our partners at MSP Marketing Edge.
It’s time to break out the crystal ball to see what 2022 has in store for business owners. Will this year finally bring us relief from coronavirus in its many forms? Will taxes go up? Will inflation go down?
Here are the four most common questions that keep business owners up at night—and our advice on how to get a better night’s sleep:
What is the Ripple Effect?
The “ripple effect” occurs when the normal flow of business is interrupted and affects every stage downstream. The ripple effect can be found in labor, supply chain, and inflation (to name a few areas of concern).
You need to ask, “what will the ripple effect do to my business?” Every time you read a business article, listen to a podcast or watch a webinar, use the ripple effect to connect the dots on what is being said to your business.
Inflation in China? What does that mean for my retail business in Chicago? Coronavirus outbreak in India? Will that hurt my company in Indiana? The quick answer may be “no,” but if your wholesalers or partners do business in those countries, it could harm your business.
Tip: Play the “What If” game with your business to spot potential ripple effects. For example: “What if my wholesaler’s supplier has to shut down due to the pandemic. How will it affect my business?” Or “What if I own a landscaping company and my customers get hit by a natural disaster? How long will my projects be delayed? Am I caught up with Receivables?” Your answers to all the “What If” questions could make the difference between getting knocked down in business versus getting knocked out of business.
Will the labor shortage continue this year?
The quick answer is yes. But depending on your business, there are options for dealing with a smaller labor pool.
Can you automate any part of your operations, like customer service or inventory control? This would allow your employees to focus on your company’s priority areas. Can you outsource any part of your business? This option also helps deal with having fewer employees.
Tip: Have you tapped into new sources of labor—retirees, friends and family, parents returning to work? One way to find new employees is by offering them the opportunity to work remotely. It is now a competitive advantage for business owners and a reward for employees.
When will my supply chain get back on track?
Probably not as soon as you would like it to be. Everything is backed up! Container ships are sitting out at sea, trucks sit in parking lots waiting for drivers, and shelves sit barren waiting for products.
Tip: This is a painful example of the ripple effect. To counter that, we recommend that you look at alternative options for sourcing materials or buying goods this year. The closer to your home base you can find them, the better your chance of minimizing the ripple effect.
Will Inflation Go Down in 2022?
According to the Federal Reserve, it should, but not right away. They plan to raise interest rates three times this year to combat skyrocketing inflation—last November’s rate was the highest in 39 years.
The first increase is planned for March, which means higher interest rates on everything from credit cards to lines of credit.
Higher inflation creates higher variable costs for your business. Gas, shipping, materials, and so on will be more expensive this year. Until we can control coronavirus, supply chain, and labor issues, inflation will continue to hover above the 5% rate, when ideally, we would have it under 2%.
Tip: Assume higher variable costs in the first half of this year. If they turn out to be lower, your company has better cash flow. If not, you won’t have to deal with negative cash flow because you built higher costs into your plan.
If you have other pressing questions, we would love to hear them and help you develop solutions to better navigate your business through the uncharted waters of 2022. Contact Yeo & Yeo today.
Information used in this article was provided by our partners at Sage.
Despite the world’s best efforts to get everyone off passwords and onto something else (e.g., MFA, password-less authentication, biometrics, zero trust, etc.) for decades, passwords have persisted. Today, nearly everyone has multiple forms of MFA for different applications and websites, and many passwords.
The average person has between three to seven unique passwords that they share among over 170 websites and services. And unfortunately, those passwords often get stolen or guessed by cybercriminals.
According to Hive Systems, any 8-character password can be cracked in less than an hour through brute force. Further, any password containing less than seven characters can be cracked instantly.

Password Attack Defenses
The password attack defenses can be summarized by the following, in order of importance:
- Use multifactor authentication (MFA) whenever possible
- Be cognizant about what you put on social media
- Use a different, non-guessable password for each site and service
- Use a password manager wherever you can to allow perfectly random passwords to be created and used
- Where a password manager cannot be allowed, users should create long and/or complex passwords or passphrases, different for each site and service
- All passwords should be changed at least annually
Whenever possible, use multifactor authentication (MFA) to provide another layer of security. The best tactic a user can do to prevent password hacking (after using MFA) is to avoid being socially engineered, which takes a good, in-depth combination of policies, technical defenses, and end-user education.
In closing, password attacks are widespread and one of the highest cybersecurity risks to any user and organization. Most password attacks happen because a user’s password (or password hash) is stolen or guessed. Users who follow the password defense recommendations above are far less likely to be hacked because of their passwords.
Information in this article was provided by our partners at KnowBe4.
Now that the cloud has become a mainstay in the business world, we’re seeing the true impact of cloud business communications.
Most companies use the cloud — 91 percent use the public cloud, and 72 percent utilize private cloud solutions. With the cloud, teams can work from anywhere—productivity increases. And the reliance on traditional phone systems and expensive hardware is over, making industry-leading business communications accessible to even small companies.
Cloud business communications have turned out to be far more than an option for cutting costs and making scaling easier. It’s shifting the way people work, collaborate, and share information. Let’s dive into the specific ways that the cloud enables business communications.
1. Teams Can Work from Wherever
With the cloud, teams can work from any location with an internet connection. Cloud phones transmit voice data over the internet, so there’s no need to be connected to a traditional PBX phone system to communicate with customers and partners. Your users can also access your cloud communications platforms from anywhere.
Because of the cloud, more businesses are shifting to remote or hybrid work models, which can create a range of benefits, including lower real estate costs, more flexible scheduling, and the ability to tap into a wider talent pool.
2. Data Is More Secure
Before the cloud, data security fell entirely on the shoulders of the company. You had to ensure all your hardware and software were maintained, updated, and protected.
With cloud business communications, your cloud provider shoulders some of the burden.
It’s still up to you to protect your devices, provide security training to employees, and follow best practices such as email encryption and multi-factor authentication. However, it’s up to them to secure their data centers and networks. This shared responsibility enables your teams to use advanced communications technology with confidence.
3. Cloud Business Communications Boost Productivity
Being able to work from anywhere and on any device is also helping to boost productivity. With cloud communication tools such as video conferencing and UCaaS (unified communications as a service), co-workers can connect virtually. They can also share files in real-time and collaborate on projects as if they were physically together.
Additionally, cloud platforms can integrate with other business applications, syncing data and simplifying work processes. Employees can access customer information, analytical insights, and other data without jumping to different applications. This saves time and reduces employee errors.
4. Cloud Technology Is More Reliable
Another way that the cloud enables better business communications is through performance. As long as you work with a provider that guarantees near-flawless uptime, your teams don’t have to worry about reliability issues. Look for a provider that offers a 99.999% uptime guarantee in their service level agreement and say goodbye to business downtime.
Empower Your Teams with Cloud Communications
The cloud has revolutionized business technology. But no area has been more profoundly transformed as much as business communications. With cloud communications, the office has become obsolete, high-level security and compliance aren’t just possible, they’re streamlined, and even low-budget companies can access powerful communications tools.
The best part is that migrating to the cloud and getting started with leading-edge cloud business communications is simple. Just reach out to the team at Yeo & Yeo Technology today and let us know your cloud communication needs. From cloud phones to integrated communication platforms, we’ll help you thrive with the cloud.
Information used in this article was provided by our partners at Intermedia.
How can I make my display more organized?
Consider adding a second monitor. This will allow you to better organize your apps and windows and give you more workspace.
Can my phone be hacked?
Yes! As well as the risk of phishing and smishing (that’s phishing via text message), you also put your data at risk by connecting to public Wi-Fi. Fake apps can be an issue too.
How do I know if my Teams app is up to date?
Click on the three dots next to your profile picture and select ‘Check for Updates’ from the menu. If you’re using Windows 11, you’ll need to check under settings -> about Teams.
Information used in this article was provided by our partners at MSP Marketing Edge.
The FBI published a public service announcement updating its warnings about the continuing threat of business email compromise (BEC, also called CEO fraud). The problem has reached shocking proportions: between June 2016 and December 2021, the Bureau counted 241,206 domestic and international business email compromise incidents. The “exposed dollar loss” (including actual and attempted losses) is the real shocker: $43,312,749,946, more than forty-three billion dollars.
At its root, BEC is a social engineering problem. “The scam is frequently carried out when an individual compromises legitimate business or personal email accounts through social engineering or computer intrusion to conduct unauthorized funds transfers,” the FBI explains.
Some variants don’t necessarily involve a direct, unauthorized funds transfer. The crooks also look for “Personally Identifiable Information, Wage and Tax Statement (W-2) forms, or even cryptocurrency wallets.”
And the problem is growing worse. “Between July 2019 and December 2021, there was a 65% increase in global exposed losses.” Part of the increase may be attributable to the growing use of cryptocurrencies, which are well adapted to fast funds transfers and have a reputation for anonymity.
“The IC3 has received an increased number of BEC complaints involving cryptocurrency. Cryptocurrency is a virtual asset that uses cryptography (the use of coded messages to secure communications) to secure financial transactions. It is popular among illicit actors due to the high degree of anonymity associated with it and the speed at which transactions occur.”
The public service announcement offers some suggestions businesses might follow to protect themselves. Some of them involve instituting sound policies, like using “secondary channels or two-factor authentication to verify requests for changes in account information” or seeing that “the settings in employees’ computers are enabled to allow full email extensions to be viewed.”
Many of them, however, are matters of training:
- Ensure the email URL is associated with the business/individual it claims to be from.
- Be alert to hyperlinks that may contain misspellings of the actual domain name.
- Refrain from supplying login credentials or PII of any sort via email. Be aware that many emails requesting your personal information may appear legitimate.
- Verify the email address used to send emails, especially when using a mobile or handheld device, by ensuring the sender’s address matches who it is coming from.
- Monitor your personal financial accounts regularly for irregularities, such as missing deposits.
These, and other points, can be addressed in new-school security awareness training that can enable your employees to recognize business email compromise.
Information in this article was provided by our partners at KnowBe4.
When did you last check if everything was okay with the devices your team uses when they work remotely? According to a report by EuroPC, 67% of remote workers are using faulty devices for work. And the reason?
They’ve likely damaged the device themselves and are too scared to tell you!
Laptops, keyboards, and monitors are most likely to be damaged (in that order). And it’s usually because of food or drink spills … though some blame their partners, children, and even their pets.
Using a device that doesn’t work properly is a problem.
First, it’s going to damage your team’s productivity. Tasks might take longer or be more difficult to complete. Employees who try to fix the problem themselves risk causing further damage. But the other issue is that of security.
In some cases, your people will stop using their damaged company-issued device and use a personal device instead, which puts your data at risk because their personal devices won’t have the same level of protection as your business devices.
It also means that if they’re connecting to your network, it might not be a safe connection, potentially leaving the door open for cybercriminals.
And because your IT partner may not monitor personal devices, they won’t spot an intrusion until it’s too late.
Our advice? Make it a routine to check that everyone’s happy with their devices. And have a policy that they won’t get in trouble for accidental damage, so long as it’s reported immediately.
If you need help replacing your organization’s hardware, contact Yeo & Yeo Technology.
Information used in this article was provided by our partners at MSP Marketing Edge.
