Cyberattacks Targeting Healthcare Organizations Surge
During the past two months, cyberattacks against healthcare organizations and companies involved in COVID-19 vaccine distribution have been on the rise.
From an upsurge in the registration of coronavirus-related malicious domains to fraudulent advertisements offering COVID vaccines for sale, we have seen an unprecedented increase in cyber-exploits seeking to compromise personal data, spread malware and steal money.
According to a new report published by Check Point Research, attacks targeting healthcare organizations have spiked by 45% since November 2020, making healthcare the most targeted industry by cybercriminals.
Of the attack vectors used, ransomware shows the largest increase and is the biggest threat to healthcare organizations when compared to other industry sectors. Ransomware attacks against hospitals and related organizations are particularly damaging, as any disruption to their systems could affect their ability to deliver critical care.
Unfortunately, cybercriminals will continue to exploit the world’s focus on the pandemic for their own illegal purposes. Both organizations and individuals must take precautions to protect themselves against online crime.
Stop cyberattacks in their tracks with YYTECH’s Security Awareness Training. Our training solution showcases best practices for a company’s first line of defense — its employees — and teaches them how to detect and prevent cyberattacks.
Learn more about how Security Awareness Training can help protect your organization.
In today’s day and age, we don’t go anywhere without our phones. Especially during the pandemic, we rely on our mobile devices to connect with family and friends. However, a 2020 study from the cloud security company Lookout suggests that our mobile devices are not as safe as we think.
According to Lookout, mobile phishing attacks grew 37% from Q4 2019 to Q1 2020, with much of this growth attributed to new attacks related to COVID-19. These attacks come from many mobile channels, including social media apps, gaming apps, banking apps and messaging services.
Common Mobile Phishing Attacks:
- URL Padding: The hacker uses a real and recognizably safe domain up front but then adds hyphens or other characters to conceal the malicious domain.
- Man-in-the-Middle Attack: A user receives a message from a trusted organization asking them to log in via their browser and verify account details. The link leads them to a malicious site that looks exactly like the organization’s real website.
- Overlay Attack: The attacker delivers a fake login screen inside the mobile app, placing the fake screen on top of the real screen.
While people are primed to receive phishing attacks on their desktop and laptop computers, they generally feel safer when using a mobile device. Regardless of what device you use, it’s important to stay vigilant online and think before you click.
Stop cyberattacks in their tracks with YYTECH’s Security Awareness Training. Our training solution showcases best practices for a company’s first line of defense — its employees — and teaches them how to detect and prevent cyberattacks.
Learn more about how Security Awareness Training can help to protect your organization.
According to Spiceworks’ Annual Report on IT Budgets and Tech Trends, 88 percent of businesses will increase their IT spending in 2021. We have identified three key things to consider when planning your organization’s IT budget for the coming year.
1. Remote Work
The coronavirus has made it abundantly clear that the need to work remotely is no longer a perk or a convenience – it’s a necessity. A recent Intermedia survey found that more than half of U.S. small business owners believe working remotely is here to stay post-pandemic. However, equipping employees with the tools needed to work from home can be a large undertaking with updates to hardware and software. In 2021, 17 percent of total hardware budgets are expected to be allocated toward laptops, which allow employees to take their office anywhere.
2. Security Awareness Training
The business shifts ushered in by COVID-19 have also resulted in increased concerns among IT departments. Both ransomware and malware attacks have risen dramatically since the start of the pandemic. From a cybercrime perspective, working remotely generally isn’t as safe as working in the office. While adapting to working from home, employees may have let their usual security procedures slide. Education is a key factor in prevention, and Security Awareness Training is a cost-effective way to train employees to notice warning signs and stop an attack before it strikes.
3. Cloud-based Services
Cloud computing centralizes information in a single cloud infrastructure that is easily retrievable for employees working from home. Cloud-based video conferencing software and phone systems can integrate all communication tools – desktop phones, mobile phones, and computers – into one manageable solution. Our cloud-based communication service, YeoVoice, allows mobile devices to interact seamlessly with the corporate phone system anywhere, anytime, and on any device, creating a more flexible workforce.
2020 has been full of change for the IT industry. Increased emphasis on remote working has resulted in new cybersecurity risks and software demands. YYTECH can help businesses identify the best solutions to these challenges. Learn more about our suite of services.
Data is commonly a company’s most valuable resource, and the level of effort made to protect it often means the difference between success and failure. In its Annual Data Security Report, GetApp surveyed 83 IT security managers to determine the top data security trends businesses should learn from going into the new year.
- Remote work security is a top vulnerability. Every facet of life has been affected by COVID-19, including data security. Companies are urged to develop work-from-home policies and adopt software tools that ensure data is safe when accessed remotely.
- Breaches are four times more likely for businesses allowing full data access. Employees should be allowed only the minimum level of data access needed to perform their jobs. Even something as simple as securing folders within Windows or limiting access to a shared Google Drive will strengthen security and decrease the chances of a data breach.
- Data classification is not enough on its own. Sixty-two percent of companies with a data classification policy still provided employees access to more data than they needed. To protect data, companies must implement data classification policies and lock down access.
- Cyberattacks continue to rise. Phishing schemes, account takeovers and ransomware attacks continue to hit businesses. Security Awareness Training can help employees recognize warning signs and stop these attacks before they strike.
- Multifactor Authentication becomes more popular. The use of biometric data security measures increased from 27% in 2019 to 53% in 2020. This sharp increase may be driven in part by the increased use of laptops and mobile devices to support remote work, as these devices commonly include fingerprint and facial recognition security features.
- Virtual training is the new norm. Offline modes of training, such as on-the-job and classroom instruction, saw decreases across the board. In contrast, the use of digital training tools (online training programs, webinars, etc.) saw an equivalent increase. 17% of businesses are even using Augmented Reality and Virtual Reality for training purposes.
Cybersecurity is more than just access controls and technology. It’s a mindset that starts with education and ends with execution. Stop cyberattacks in their tracks with YYTECH’s Security Awareness Training. Our training solution showcases best practices for a company’s first line of defense — its employees — and teaches them how to detect and prevent cyberattacks.
Source: GetApp Annual Security Report
One of the most prevalent means of cybercrime is phishing sites. Here, criminals create a seemingly authentic copy of a popular website to lure people into entering their sensitive data, be it account login credentials or credit card information.
Since the beginning of the year, Google has flagged 2.02 million phishing sites, averaging 46,000 sites per week, according to researchers at Atlas VPN. Researchers note that the number of phishing sites peaked at the start of the year, which correlates with the beginning of the pandemic.
Data also reveals that in the first half of 2020, there were two huge spikes in malicious websites, reaching over 58,000 detections per week at the peaks. Atlas VPN says the number of new phishing sites has been steadily increasing each year since 2015, but it’s now higher than it’s ever been.
To look at the broader perspective, Atlas VPN analyzed phishing site data since the first quarter of 2015. Their findings revealed that the year 2020 is, in fact, the year with most new phishing sites to date.
Researches attribute the spike in 2020 to the COVID-19 pandemic, as people are spending more time online and emotions are running high. Panic resulting from the pandemic often leads to irrational thinking, and people forget basic security steps. Users then download malicious files or try to purchase in-demand items from unsafe websites, in result becoming victims of a scam.
Google and other companies do a good job of tracking down malicious sites, but attackers can easily scale their operations and set up new sites to stay ahead of efforts to shut them down. New-school security awareness training can enable your employees to spot these sites on their own.
Stop cyberattacks in their tracks with Yeo & Yeo Technology’s Security Awareness Training. Our training solution showcases best practices for a company’s first line of defense — its employees — and teaches them how to detect and prevent cyberattacks.
Learn more about how Security Awareness Training can help protect your organization.
Information used in this article was provided by our partners at KnowBe4.
Social media provides a platform to connect with friends during the pandemic. But data from the Federal Trade Commission’s (FTC) Consumer Sentinel Network suggests that social media websites and apps have become popular hangouts for scammers, too. According to the FTC, reports that people lost money due to social media scams more than tripled in the past year, with a sharp increase in the second quarter of 2020.
In 2019, total reported losses to social media scams reached $134 million. But reported losses reached record highs, climbing to nearly $117 million in just the first six months of 2020. In that time, the reported social media scams often related to online shopping, romance scams and supposed economic relief.
- Online shopping. Online shopping scams occur when cybercriminals create illegitimate shops and trick victims into paying for products that are never delivered. Attackers can make realistic ads that are carefully targeted to reach a particular audience. They can even delete comments on these ads so that negative responses don’t show up and alert people to the con.
- Romance scams. Romance scams typically start with a social media message or friend request. They often target people who are on dating sites. In Q2 of 2020, 2,621 people reported a monetary loss on a romance scam, a 19% increase over the previous quarterly high.
- Economic relief. Economic relief scams offer so-called relief to people in need of cash. Scammers pretend to provide grant money and other giveaways, supposedly to help people during the pandemic. Messages can even come from friends who may have been hacked or don’t know the offer is a scam.
Cybercriminals continue to use the pandemic as an opportunity to take advantage of social media users. As always, be mindful when using social media for business or personal use.
Stop cyberattacks in their tracks with YYTECH’s Security Awareness Training. Our training solution showcases best practices for a company’s first line of defense — its employees — and teaches them how to detect and prevent cyberattacks.
Learn more about how Security Awareness Training can help protect your organization.
Some of the information used in this article was provided by our partners at KnowBe4.
CRM software offers your organization the tools you need to thrive in today’s business environment. It delivers critical information about your prospects and customers to the people who need it, when they need it. It tracks your follow-ups and reminders and ensures that no one misses a beat when it comes to taking care of business.
We now live in a customer experience economy. Prospects and customers are calling the shots, and competitors are just a click away. Businesses must provide consistent, high-quality experiences to drive sales. However, most companies can’t deliver these experiences by continuing to do business as usual.
Too many companies rely on silos of information, locked away in Outlook and Excel, invisible to members of other teams and departments. This limits their ability to respond quickly and accurately when customers need them. It doesn’t scale, resulting in missed opportunities and lost business, even from long-time customers.
CRM helps you
- Get organized and stay connected as a team
- Standardize, automate and track tasks
- Work from anywhere on any Internet-capable device
- Understand what your team is doing and how well it is working
- Stay connected to your customers
What does this mean for your business?
- Increased sales per salesperson
- Increased sales per customer
- Reduced customer turnover
YYYC Can Help You Implement a Customized CRM Software.
We offer two highly customizable CRM software options, Sage100 CRM and Microsoft Dynamics 365 Sales. Find out which CRM software would best fit your organization, contact YYTECH today.
Generally, there are two important elements when it comes to turning leads into customers and keeping them happy and loyal: strong personal skills and an efficient customer relationship management (CRM) software.
CRM is, in its broadest sense, a technological Rolodex that does much more. In effect, the software offers unified views of clients, contacts, calls and notes that make it simpler to keep track of the marketing pipeline from the first contact through the signing of a deal.
These systems allow you to manage your sales process more effectively and forecast sales and project revenue more accurately. They also free up sales reps to spend more time in the field closing deals.
But some specialists estimate that from 35 to 70 percent of businesses fail in their first attempts to install and operate a CRM. Among the reasons are:
- Too much focus on technology. CRM applications come in various shapes and sizes, and you need to choose one that best suits your business and doesn’t have unnecessary bells and whistles. The primary functions of CRM systems are to streamline front-office operations, display key information about marketing, sales and customer support, and make your business processes more efficient and cost-effective. When considering a CRM application, if you don’t need a feature, don’t buy it.
- Too little focus on the customer. The core of any CRM system is your company’s customers and their needs. A call-center can be a great help, provided it is customer friendly. If the system is too complicated it can alienate customers, sales leads, and your staff.
- Too little preparation. The people who will be using the system will likely have different needs and expectations. For example, a CFO will want to view the entire pipeline to calculate budgets, while the sales team will be more interested in call scheduling and ease of data entry. Take your time to consider how everyone will use the system, how your IT staff will cope with it and whether you need to create new departments to deal with it.
YYYC Can Help You Implement a Customized CRM Software.
We offer two highly customizable CRM software options, Sage100 CRM, and Microsoft Dynamics 365 Sales. Find out which CRM software would best fit your organization, contact YYTECH today.
Your sales team needs more than traditional sales force automation to respond to today’s unpredictable selling environment — rapidly changing buyer preferences, sudden changes in business outlook and fast-moving competitors. Dynamics 365 Sales is an adaptive selling solution that helps your team navigate the realities of modern selling.
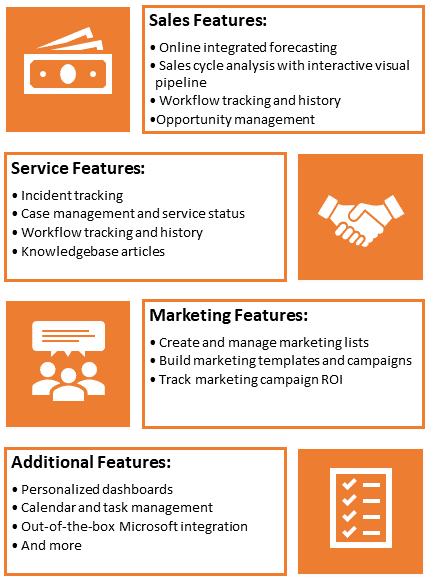 Dynamics 365 Sales offers Enterprise-level value at SMB prices. It’s more powerful than typical SMB solutions and scales extremely well. It integrates seamlessly with other Microsoft programs that you know and love, creating a comfortable and intuitive experience for your team. As a Microsoft product, Dynamics 365 Sales receives continuous improvement and support, ensuring that your business has the best product available.
Dynamics 365 Sales offers Enterprise-level value at SMB prices. It’s more powerful than typical SMB solutions and scales extremely well. It integrates seamlessly with other Microsoft programs that you know and love, creating a comfortable and intuitive experience for your team. As a Microsoft product, Dynamics 365 Sales receives continuous improvement and support, ensuring that your business has the best product available.
According to Gartner, Dynamics 365 Sales is a top leader in CRM, offering flexibility, integrations and capabilities that most software lacks. It provides a high-power, low-cost solution viable for any size business.
YYYC Can Help You Implement a Customized CRM Software.
Find out which CRM software would best fit your organization, contact YYTECH today.
According to Bitdefender’s Mid-Year Threat Landscape Report 2020, the first half of 2020 saw a 7x jump in the frequency of ransomware attacks compared to the same time in 2019. Likewise, the price of ransoms has jumped by an average of 60 percent, making it more expensive for organizations to get their stolen data back.
Both the pandemic and the shift to working from home play a significant role in the success rate of attacks, as users have their defenses down and have been overwhelmed by the unprecedented change in the way we all work and live. As we adjust to new work arrangements, here are ten useful tips to help you and your employees detect and prevent cyberattacks:
- Don’t click on direct links (in emails, text messages, etc.), especially those asking you to enter sensitive information. It’s best to go directly to the source.
- Don’t overshare on social media. These details can provide hackers with your location, ammunition to craft spear-phishing attacks and answers to security questions. Think before you share!
- Don’t go “out of bounds” for communication. If you’re buying something on eBay and the other party wants to negotiate via email instead of the bidding system.
- Never reuse passwords between any website or service.
- Always be skeptical of any unexpected invoice, or request to get or pay for anything by using gift cards.
- Never answer authentication recovery questions (e.g., What is your mother’s maiden name?) with real answers. Unfortunately, that means you’ll have to write down each question and answer for each website that requires them, but you’ll be far less likely to have your account hijacked.
- It is OK to confirm an email sender’s request, even if it is your boss. Better safe than sorry.
- Know who to report any suspicious emails to at your workplace. Don’t delete the email – report it.
- Invest in a password management tool – ain’t nobody got the time to remember all those passwords!
- Be vigilant with suspicious SMS messages. Your bank will NEVER ask you to access your account from an SMS.
With such massive increases in the number of cyberattacks in 2020, organizations should assume that ransomware and other scams will only become more prevalent, pervasive and profitable for the bad guys.
Stop cyberattacks in their tracks with YYTECH’s Security Awareness Training. Our training solution showcases best practices for a company’s first line of defense — its employees — and teaches them how to detect and prevent cyberattacks.
Learn more about how Security Awareness Training can help protect your organization.
Information used in this article was provided by our partners at KnowBe4.
In the wake of the COVID-19 pandemic, many people have found themselves working from home. From a cybercrime perspective, working remotely generally isn’t as safe as working in the office. In fact, studies show that cyberattacks like ransomware are on the rise.
With the ever-increasing popularity of remote work, here are three reasons why cybersecurity monitoring is more important than ever before.
1. Increased efficiency and detection:
With more people working from home, more devices are being connected to your organization’s network. Security analysts can get stretched thin and hit efficiency roadblocks, especially as they gather and analyze alarm data from multiple platforms. Studies show the average time between a data breach and discovery is 205 days – that’s over 7 months! Continuous monitoring systems can help your organization immediately detect threats and stop them in their tracks.
2. Ensured industry compliance:
Organizations that fall under PCI, HIPAA or FFIEC regulations must implement technical safeguards to protect their clients’ data. If cybercriminals breach your organization, you must prove to authorities that you took measures to guard sensitive data. Utilizing continuous monitoring software helps fulfill these compliance requirements, making it easier to avoid fines after an attack.
3. Heightened security measures:
While adapting to working from home, employees may have let your usual security procedures slide, from accessing your company’s IT environment with personal Wi-Fi connections to using unprotected video conferencing tools. Continuous monitoring creates another security layer for your company and employees, especially as they work remotely.
YYYC can support your IT team in the defense against cyberattacks with YeoSecure.
Our comprehensive cybersecurity monitoring and compliance solution, YeoSecure, transforms the way companies detect, investigate and respond to cyber threats. YeoSecure provides 24/7/365, enterprise-grade cybersecurity monitoring and support while cutting costs and keeping your IT team from scrambling to detect and troubleshoot cyberattacks.
Learn more about how YeoSecure can help your organization detect, respond, and comply.
COVID-19 has forced educators to rethink how they teach and interact with students. As many children return to school, the main priority is keeping them safe without compromising their education.
Yeo & Yeo has partnered with Link Technologies to offer Ergotron mobile desks with clear vinyl safety shields. These desks allow teachers to easily arrange classrooms to meet social distancing requirements. They also decrease sedentary time, improving students’ physical health and engagement.
Safety Shield Features:
- Inexpensive added measure of protection
- Double polished, optically clear, high strength, automotive-grade vinyl
- Lightweight
- Combinations can be easily configured for a variety of desktop sizes and uses
- Excellent sound transmission as compared to polycarbonate
- Easily installed, removed and cleaned/disinfected
- UV resistant
- Made in Michigan
Optically clear, Smart Shield-protected mobile desks provide the flexibility and safety that our new normal demands. Learn more about YYTECH’s Ergonmic Solutions.
As COVID-19 forces businesses to rely on online systems to operate, ransomware attacks are on the rise. On October 1, the U.S. Department of Treasury issued an advisory statement to victims who may attempt to make ransomware payments.
According to the Treasury, paying cybercriminals encourages future attacks and does not guarantee that the victim will regain access to stolen data. Therefore, victims who pay the ransom to get their data back could face significant fines from the Treasury’s Office of Foreign Assets Control (OFAC).
How Can I Protect My Business?
Typically, ransomware takes over a victim’s machine and demands money in exchange for access to stolen information. The best way to prevent ransomware attacks is to create offline data copies, also known as air gap backups. The concept is simple: devices that aren’t connected to a network cannot be attacked remotely.
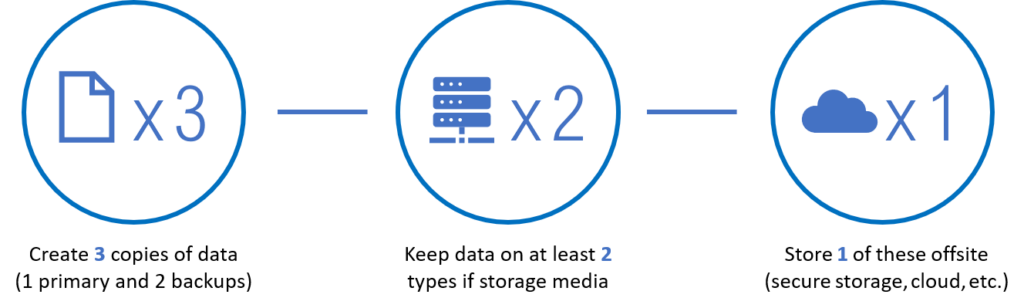
Using the 3 – 2 – 1 Backup Strategy
The most common way to create air gap backups is the 3 – 2 – 1 strategy. First, the company makes three copies of their data, one primary copy and two secondary copies. Next, the data is stored in at least two different types of media. One of these types of media is then kept offsite in a secure location.
YYYC can support your IT team in the defense against cyberattacks with YeoSecure.
Our comprehensive cybersecurity monitoring and compliance solution, YeoSecure, transforms the way companies detect, investigate and respond to cyber threats. YeoSecure provides 24/7/365, enterprise-grade cybersecurity monitoring and support while cutting costs and keeping your IT team from scrambling to detect and troubleshoot cyberattacks.
Learn more about how YeoSecure can help your organization detect, respond, and comply.
Small and midsize businesses across the country have pivoted to remote-work as a necessity. Looking into the future, businesses will need to embrace remote-working with flexibility in mind.
With employees working between a mix of offices or remotely, your communication systems need to be flexible and reliable. Cloud-based communications platforms that including business phone, chat, video conferencing and more will help your business remain successful as we transition in this new environment. Read our PDF below to learn why Working Remotely is Here to Stay.
Read New Study Finds More Than Half of U.S. SMB Owners Believe Working Remotely Is Here to Stay Post-Pandemic and learn about:
Read “Working Remotely Is Here to Stay”
- Video conferencing is the “new’ face-to-face meeting
- Remote working isn’t temporary
- Flexible work environments lead to happier employees
Are you ready to learn more about how YYTECH can help you implement a remote-working strategy? Contact us today.
October is National Cybersecurity Awareness Month (NCSAM) and 2020 marks the 17th year since the National Cyber Security Alliance started the initiative. This year, the theme is, “Do Your Part. #BeCyberSmart.” The theme empowers individuals and organizations to own their role in protecting their part of cyberspace, with an emphasis on the key message for 2020: “If you connect it, protect it.”
If everyone does their part – implementing more robust security practices, raising community awareness, educating vulnerable audiences or training employees – our interconnected world will be safer and more resilient for everyone.
The NCSAM suggests the following steps to #BeCyberSmart:
- Never click and tell: stay safe on social media
- Update privacy settings
- Keep tabs on your apps: follow best practices for device applications
- Shake up your passphrase protocol: create strong, unique passphrases
- Double your login protection: turn on multi-factor authentication
- Shop safe online
- Play hard to get with strangers: learn how to spot and avoid phishing threats
- If you connect, you must protect: update to the latest security software, web browser, and operating systems
- Stay protected while connected: ensure Wi-Fi safety
- If you collect it, protect it: keep customer/consumer data and information safe
Questions you should ask yourself include:
- Have I provided cybersecurity training for my staff?
- Are security policies and procedures in place?
- Has a security audit been completed recently?
Remember, a great way to spread the word on social media for this year’s NCSAM campaign is to read and share cybersecurity best practices on social media using the hashtag #BeCyberSmart.
Learn more, get involved and do your part to make the internet safer and more secure for everyone by visiting staysafeonline.org/ncsam.
YYTECH has a catalog of cybersecurity articles that can also be shared, and remember that YYTECH can help ensure your data is protected.
Cybercrime is real, and it’s increasing …
Mobile and Apple/iOS attacks on the rise. Phishing attacks targeting Apple products has hit a new high this year, with around 1.6 million campaigns currently trying to target iOS and Mac devices.
99% of all email attacks rely on a victim clicking on a link.
CEO Fraud, a scam in which cybercriminals impersonate executives, continues to increase. FBI statistics show that CEO fraud scammed over $26 billion from victims between June 2016 and July 2019. CEO fraud increased by 100 percent between May 2018 and July 2019.
YYTECH can help protect your organization with these preventive services:
YeoSecure is 24/7/365 security monitoring of networks and is designed to prevent and accelerate the detection of cybersecurity threats.
Security Awareness Training showcases best practices for a company’s first line of defense — its employees — and teaches them the dangers of online threats.
As always, remember to be aware and think before you click!
Just-released data from cyber insurer Coalition shows massive increases in both the frequency of ransomware attacks and the ransom demand with Maze and Ryuk leading the way.
We’ve been seeing more and more cybercriminals turning to ransomware as a go-to strategy to generate their criminal revenue. Many are turning to using both encryption and the theft and threatened publishing of victim data to double-up the chances of getting a payoff. This has led to hearing about larger and larger ransoms demanded.
Cyber insurer Coalition’s H1 2020 Cyber Insurance Claims Report points out the increases are more than just anecdotal. According to the report in the first half of 2020:
- Ransomware attack frequency increased 260%
- Ransom demands increased 47%
- Maze and Ryuk ransomware variants represented 53% of all attacks
- Ransoms ranged from $1,000 to over $2,000,000
According to Coalition, over half (54 percent) of attacks used email phishing attacks as the initial attack vector.
This massive increase is concerning. Organizations need to see these trends and heed their warning. With phishing being the primary vehicle, and remote workers being a consistent enabler of attacks, it’s time to educate your users via new-school security awareness training on both why and how to have security top of mind when using email and the web.
Ransomware gangs are only getting more cunning and greedy. The impact of their attacks will likely worsen, so it’s time to create a strong human firewall to stop these attacks to avoid becoming just another claim.
Article provided by our partners at KnowBe4.
A recently discovered threat targeting Windows Servers, called Zerologon, allows any device connected to a network to obtain domain admin rights with no authentication required. The flaw presents a specially crafted network command to the environment servers, bypassing user login information. The attacker will have the ability to take control of the Domain Controller and obtain domain administrator permissions (highest level security rights).
Once the attacker has obtained domain administrator permissions they can do anything they want in the environment. This vulnerability has already been weaponized into a script that any attacker can easily run once in a client environment, which makes this threat very serious.
Microsoft has released a patch for Domain Controllers to eliminate the vulnerability and it has been applied to all YeoCare clients. YYTECH strongly encourages all clients to apply this patch as soon as possible. Please contact your YYTECH representative if you have any questions about how to apply the patch.
Contact YYTECH if you have any security questions regarding Zerologon.
The information security landscape seems to evolve at a faster pace with each passing year. For organizations of all sizes, it’s critical to not only remain up to date on current attack techniques and defenses but also to look ahead at potential security developments and circumstances that have yet to come. That’s why each year, the research team at Forbes takes a step back to develop a series of predictions about emerging security trends that could have the biggest impact, new threats that might rear their ugly heads, and how cutting-edge attacks will affect the industry.
Let’s take a look at three key cybersecurity predictions for 2020 — and what you need to know to prepare:
- The Cybersecurity Skills Gap Will Widen
The cybersecurity industry has exploded over the past decade. As the realities of data breaches and online attacks have penetrated mainstream consciousness, demand for skilled security professionals is at an all-time high. However, the current supply isn’t sufficient. A recent (ISC)2 study found that businesses are currently suffering a cybersecurity workforce gap of over 4 million employees (up from a gap of 1.8 million in 2017). And according to one ESG report, 29% of organizations see insufficient security staffing as their top challenge, while 74% have already witnessed the cybersecurity skills gap take a toll on their business.
Unfortunately, targeted adjustments in security education and recruiting aren’t likely to take effect quickly enough to right the ship in the immediate future. As there continues to be a swell in demand for skilled infosec professionals, the cybersecurity skills shortage will continue to increase in 2020. Until this can quell growing scarcity, organizations will be forced to find other ways to prevent advanced and frequent cyberattacks.
The good news is that more and more managed service providers (MSPs) have taken notice of the opportunity and begun to offer specialized security services. With the availability of both cloud-managed, layered security protections and the managed security service providers (MSSPs) to deliver them, enterprise-grade security has never been as simple, accessible, and cost-effective for businesses of all sizes as it is today. In the face of this ongoing security skills shortage, organizations of all types and sizes will engage with MSSPs to outsource their security needs.
- Ransomware Will Target The Cloud
Ransomware has been a major payload for cyber criminals over the past decade. To rake in profits, hackers have moved away from the “shotgun blast” approach to ransomware attacks (pursuing as many victims as possible) in favor of targeting healthcare providers, governmental groups, industrial groups , and other organizations for which downtime is unacceptable. These targets are most likely to pay to resolve a ransomware infection quickly. Anticipate that cybercriminals will begin using ransomware to target public cloud properties.
One reason the cloud represents such an enticing target for attackers is that it’s now a critical uptime resource for vital network and web applications. Beyond that, the cloud also offers an attractive central aggregation point ransomware attackers can leverage to access a much larger pool of victims simultaneously.
According to research from WachGuard, legacy signature-based anti-malware services fail to block half of today’s evasive malware attacks. As ransomware variants continue to become more evasive, organizations must deploy more proactive malware detection solutions that leverage advanced behavioral analysis with cloud sandboxing and machine learning.
Because many businesses rely heavily on cloud resources for day-to-day operations, deploying these advanced antivirus solutions in cloud environments will be key to preventing cloud-specific ransomware attacks in 2020. Every organization using cloud architecture today — whether it be a public or private cloud — can and should harden those environments using basic techniques like securing their S3 bucket configurations, closely managing file permissions, requiring multifactor authentication for access, and more. Finally, one benefit the cloud offers is automated backup and imaging of resources as part of version control. Be sure to leverage these features to quickly recover to a clean state if you ever suffer a cloud store ransomware attack.
- Individual States Will Enact Regulations Inspired by GDPR and CCPA
It’s been two years since the European Union came out with the General Data Protection Regulation (GDPR) to better protect the privacy of its citizens’ data. The level of protection the law provides to individuals has been immensely popular among consumers to date, and companies like Google and Marriott have already faced fines for their violations. As organizations continue to mishandle the data of American citizens whose appetite for privacy is growing by the day, in 2020, 10 or more states will enact privacy laws similar to GDPR.
California has already passed its own California Consumer Privacy Act (CCPA), which will begin administering fines by midyear. Although some lawmakers are pushing for a similar regulation at the federal level, don’t believe the movement will gain the support it needs this year. Why? This is based on the fact that most individual states passed mandatory data breach disclosure laws in the mid2000s (led again by California in 2002), but a federal version still hasn’t passed yet. So to better protect their citizens quickly, expect this state-level trend will continue.
Individuals concerned with personal privacy should petition their local representatives for state-level regulations and advocate for federal action as well. For businesses across the country, it will be important to proactively study CCPA requirements, as it will likely serve as a template for new states working to roll out their privacy regulations.
As we move deeper into 2020, it will be important for your business to keep up to date with these trends — and their long-reaching implications in near and future years.
*Article provided by PartnerOn and Forbes.
Many organizations have changed how they do business and communicate. As you look to restart your operations, it’s important to consider implementing a unified communication strategy.
We understand that every organization and its employees are in a sensitive situation as they return to work, stay remote, or consider a hybrid of both. With your employees scattered, it’s vital to have a communication system that you can trust in place.
Download our PDF “Sustaining Business in an Uncertain World” to learn more about many of the steps utilized in a unified communication strategy and why unified communication systems are a must-have for remote or in-office workers.
Read “Sustaining Business in an Uncertain World”
Unified communication systems are more than just phones; they incorporate many tools to help your employees stay productive regardless of their work location. Consider the following benefits that unified communications provide.
Full Cloud Communication System: Highly reliable phone service for making crystal clear calls, plus chat, file sharing, video conferencing, and more, all rolled into a single platform – accessible from virtually any device, anytime, anywhere.
Video Conferencing: Meet from anywhere with high-quality 720p HD video and audio meetings, and don’t sacrifice the benefits of a ‘face-to-face’ meeting.
Webinar Platform: Telling your story to customers is easier with a reliable platform. Presenters can use video, audio, and screen sharing to market products and services to audiences anywhere. It can help build personal connections, engagements, and trust by simply allowing attendees to see the presenter in real-time and engage through Q&A and live polls.
If you would like to learn more about how YYTECH can help you implement a unified communication strategy, contact us today.