Office 365: Get the Business Tools You Need to Look Like a True Professional
We know how important it is for small companies to look utterly professional–right down to their business documents. The right tools can help them seem a lot bigger than they actually are.
In this video from Microsoft, watch as entrepreneur Trevor Cressey and his team take advantage of more than 100 customizable invoice templates in #Office365 to show their customers a polished, professional look. They can easily customize their invoices using built-in themes and colors. And they can add their own logo and business information for a “pro” appearance that’s on a par with any global corporation.
Yeo & Yeo Technology can help you show the world a professional face too. Contact us to find out how.
© 2018
Complete Your 2018 Security Risk Assessment and Plan for 2019
The Health Insurance Portability and Accountability Act (HIPAA) requires that practices participating with Medicaid and Medicare conduct an annual Security Risk Assessment (SRA) of their healthcare organization. The required SRA ensures your organization is compliant with HIPAA’s
safeguards. Healthcare providers looking to maximize their reward from the Quality Payment Program are also required to complete an annual SRA.
Beware of the penalties if your organization does not comply. If you do not report an SRA from the 2018 year, a 5% Medicare penalty will be applied in 2020, and the proposed noncompliance penalty for the 2019 reporting year is a 7% Medicare penalty in 2021.
To help you fulfill your annual HIPAA requirements by year end and maximize your investment in the required assessment, Yeo & Yeo and its affiliates have partnered to provide an SRA that is budget-friendly, efficient and useful. Our assessment covers all 72 HIPAA security safeguards and functions as a beneficial tool for organizations looking to develop stronger data security measures.
- Proof of HIPAA compliance
- Detailed, customized report including all compliance documents
- Identification of potential risks and vulnerabilities in confidentiality, integrity and availability of electronic patient information (ePHI)
- Comprehensive tool to develop a risk management plan
- Complimentary findings analysis review
- Less invasive than traditional assessments and requires minimum assistance from your staff
Contact us today for a quote on your annual Security Risk Assessment.
Maya Angelou once wrote, “If you don’t know where you’ve come from, you don’t know where you’re going.” In this article we’ll take a look back in time to understand the trends and breakthroughs that have led us to the era of Hyper-Converged Infrastructure (HCI).
Hyper-Converged Infrastructure (HCI) is an IT framework that combines computing, storage and networking functionality into an appliance. HCI systems provide computing, networking and storage functionalities through the same server-based resources or nodes, which creates a simple, easy to manage, single resource pool. HCI nodes combine to create clusters or pools of shared capacity, memory and computing power. These clusters are infinitely scalable and managed via a single interface, making HCI easier to support.
So how did we get here? HCI is the intersection of a few trends, scientific ‘laws’ and the maturation of the underlying and enabling .
Here’s a look into the trends that lead to HCI.
In the late 1990s, higher processor performance from Intel and Linux/open source adoption created the first major building block of HCI, storage virtualization. As storage virtualization improved, it led to server virtualization fueled by companies such as VMware. In 2011 we saw the emergence of converged infrastructure where core aspects of a data center — storage, compute, networking and server virtualization — are combined into a single chassis. Finally, in 2014 we started to see the emergence of Hyper-Converged Infrastructure, which further consolidated data center elements into a single appliance with software-defined functionality.
Now onto the laws, trends and general postulations that predicted and predicated HCI .
Our collective knowledge is always growing. Buckminster Fuller created the “Knowledge Doubling Curve” in 1982; he noticed that until 1900, human knowledge doubled approximately every century. By the end of World War II, knowledge was doubling every 25 years and he postulated that by 2000, human knowledge would double every year. Current estimates say that we’re getting close to the doubling of knowledge every 12 hours. This increasing volume of knowledge translates to massive amounts of data that must be stored, correlated, made readily available to customers, and ultimately mined for value.
We know that Moore’s law is the observation that the number of transistors in a dense integrated circuit doubles approximately every two years, which means that chip performance, and hence computing power, will increase roughly along that same curve. Moore’s prediction proved accurate for several decades, but the growth rate started to slow in 2012. Although not technically a law, Moore’s observation still holds true in that computing power is increasing every year.
A 2005 Scientific American article titled “Kryder’s Law” observed that magnetic disk areal storage density was then increasing very quickly. The pace of increased disk storage density was much faster than the two-year doubling time of semiconductor chip density posited by Moore’s law –about every 13 months. While Kryder’s growth rate predictions didn’t hold up over the long haul either, the general trend that storage density is increasing yearly remains true.
Still with us?
Let’s sum it up: Knowledge (i.e., data) is increasing yearly, compute power is also increasing, and so is storage capacity. One thing that isn’t increasing is space, as in the available physical space, in your data center. Which is why you need systems that can handle more data and provide more computing power in a compact form factor.
Since these trends will continue to grow, you’ll also need a solution that scales easier as your needs increase. This solution is Hyper-Converged Infrastructure. HCI can lower infrastructure total cost of ownership by requiring less hardware, thereby lowering your data center footprint, which results in lower power, cooling and maintenance costs. HCI nodes and clusters are infinitely scalable — just add another node to increase resources. Hyper-Converged Infrastructure is the next phase in the evolution of the data center and can help you meet your IT needs now and grow with you into the future. Check with your Lenovo business partner to see if HCI is right for your business.
Having a strong password associated with your QuickBooks file is important for two reasons:
1. It will help keep external hackers from accessing your financial information.
2. It will keep internal staff members from accessing information.
It’s easy to get your head around number 1 but what about number 2? Yes, there are those rare times when an employee may not be as trustworthy as you had hoped. And he or she may be able to view or even manipulate data in QuickBooks, simply because of a weak password or because it was shared. There also may be data you don’t want certain staff members to see.
Layers of Security
Besides just requiring a password to get into QuickBooks, Intuit has extra layers of security for users. One layer requires a person attempting access to QuickBooks to verify that he or she is authorized to use the file. Another has to do with credit card information. If a user stores customer credit card data in QuickBooks, or has the “credit card protection” feature turned on, a password must be created to get into the software.
The final layer is for the administrator of the account. QuickBooks will notify the admin if other users haven’t set up a password. The admin will have the ability to recommend other users create a password or the admin can assign a password to a user.
Here are other security tips to ensure data safety:
- All users should have a password for their QuickBooks desktop file.
- Users should choose a strong user name and password. Use unique combinations of letters, numbers and characters (such as $ and %) in a password — not basic words that can easily be found online or in the dictionary.
- Users should protect all personal information. Don’t share a user name and password with others or let colleagues sign in with your information. Make sure to use different passwords for each account.
- Users should be using the latest version of QuickBooks or on versions released within two years back. Those versions have the most up-to-date security features.
- What if a user needs to share a QuickBooks file? It’s recommended he or she use a secure method such as the Accountant’s Copy File Transfer (ACFT) service, when sharing QuickBooks files.
So, yes, passwords can be a pain to come up with and update. But the real problems will begin if your data is hacked or money is stolen from your business. So, keep things easy. Make your passwords difficult.
© 2018
Bring the power and flexibility to your IT infrastructure with Hyperconverged infrastructure (HCI) solutions from Lenovo and Nutanix. Lenovo HX Series appliances powered by Nutanix software are fully integrated, turnkey solutions that eliminate complicated setup, integration, and operation, solving the challenges faced by growing or large organizations.
In this infographic we’ll look at the top reasons to deploy hyperconverged infrastructure for enterprise applications including:
- Faster Time to Value
- Predictable performance
- Predictable performanceBuilt-in resiliency and protected data
- Faster development
- Non-disruptive upgrades and simpler scaling
- Lower Total Cost of Ownership (TCO) and higher ROI
Learn more about Hyperconverged Infrastructure and how it can help your business by reading the Lenovo infographic below.
View Infographic
Be Cyber Savvy. It’s a Shared Responsibility
- Never trust an email and remember your training to think before you click.
- Practice good password management.
- Use mobile/personal devices safely – set a pin, maintain updates, click only from trusted sources, do not save or share sensitive data.
- Use public wireless hot-spots wisely and be aware of who could be lurking over your shoulder.
- Never leave devices unprotected/unattended in public.
Protect client data.
At Yeo & Yeo, we take our clients’ data security seriously. We have reasonable measures in place to keep client
data secure. You can do the same for your organization by remembering to:
- Use client portals and encrypted email when sending sensitive data.
- Keep clients’ (and personal) sensitive data off your local computers and mobile devices.
- Do you train your staff?
- Do you have policies and procedures in place?
- Have you completed a security audit recently?
Additional cybersecurity-related articles can be found here
Cybersecurity Statistics
| Companies will spend $1 trillion on cybersecurity in the next five years. |
| 43% of cyber attacks target small businesses. |
| An average of 3,809,448 records are stolen from breaches every day. |
| The total cost for cyber crime committed globally has reached $100 billion. |
More than $1 million is lost every minute to cyber-crime. That staggering stat comes to us by way of RiskIQ who published new research showing that despite businesses spending roughly $171K every minute on cyber security, $1.1M is lost to cyber-crime.
Their research found that every 60 seconds:
- 1.5 organizations fell victim to ransomware attacks, with an average cost to businesses of $15K
- A new site appeared running the CoinHive cryptocurrency mining script
- Four potentially vulnerable web components were discovered
It also found that a new phishing domain appears every five minutes, and a new site running the CoinHive cryptocurrency mining script was detected every 10 minutes.
In an email to Info-security, security author Raef Meeuwisse said that cyber crime continues to be a profitable industry, and cyber-criminals continually evolve their tactics to remain one step ahead of the average cyber-security function.
He said: “Cyber-crime and cyber-security co-exist in a constant cycle of innovation. As one particular criminal trend towards a particular technique increases, so the security functions create or strengthen the required defenses.
“However, it is evident at both the level of personal and organizational cyber-security that spending is usually too low. In fact, most of these cyber-criminals are not going after the hard targets with great defenses, they are targeting the low-hanging fruit – and there is still far too much of it.”
RiskIQ CEO Elias Manousos said, “Leveraging the latest research as well as our own global threat intelligence, we’re defining the sheer scale of attacks that take place across the internet to help businesses better understand what they’re up against on the open web.”
Remember that your employees are your last line of defense against a cyberattack.
We live in a world where change is the only constant. As data volumes explode and customers’ response times shorten, we need IT systems that can meet those challenges now and grow with us into the future, and it’s intelligent software that provides that path.
We carry software-defined phones, drive (or ride in) software-defined cars, so why should our data centers be any different? The software-defined data center (SDDC) marks the next evolution in infrastructure and data center automation architecture.
This analyst report from Gartner defines what an SDDC is, talks about which business models and projects are best for an SDDC implementation, examines risk mitigation strategies and talks about the skills needed for a successful SDDC. It will help you decide whether an SDDC is right for your organization and guide your decision-making process as you evaluate SDDCs. If you are thinking about SDDC, Software Defined Storage or Hyperconverged Infrastructure, read on to learn more about the what, where, how and why of the Software Defined Data Center.
This report will help you:
- Learn about software-defined data centers
- Understand SDDC attributes and taxonomy
- Determine I&O skills refresh and cultural shift required
- Establish an SDDC when the business case makes sense
- Identify the business models and IT projects that get the most value from an SDDC
- Know the required characteristics to make SDDC possible
- Plan to mitigate the top risks of an SDDC project failure
View The Report
Every so often, takes a giant step forward. Think back to the first time you saw a smartphone or used a tablet. Those were huge advances in the world of . As the devices we use continue to advance, so too must the security we use to protect our information. The types of threats that lurk over the internet are making similar, giant, advances.
Every organization uses a firewall to protect themselves from outside threats. Now, Next-Generation Firewalls (NGFW) are being deployed to thwart attacks
in a more sophisticated way. According to Gartner, NGFWs are defined as deep-packet inspection firewalls that move beyond port/protocol inspection
and blocking to add application-level inspection and intrusion prevention, and bring intelligence from outside the firewall. That is a pretty daunting
definition. To have a better understanding of this description, let’s look at the differences between a traditional firewall and an NGFW.
The traditional firewall has two main functions. First, the traditional firewall controls traffic allowed to enter and exit a point inside a network. Second, traditional firewalls have Virtual Private Network (VPN) capabilities. When you look at the functionality of an NGFW, you have to break down the features of Unified Threat Management (UTM). The features under the UTM are what make NGFWs worth the investment. The added features of UTM consolidate multiple network security functions into one device. In addition to the functionality of the traditional firewall, NGFWs feature:
- Integrated Intrusion Prevention System
- Advanced Threat Protection
- Application Control
- Web Filtering
- Antivirus
- Antispam
- Antimalware
UTMs are designed to cover the entire threat network and provide the ability to stay ahead of the latest vulnerabilities.
All of this information is great and sounds technical, but let’s get down to the bottom line: Is an NGFW right for you? The reality is NGFWs are the best and most efficient way for small and mid-sized businesses to manage the latest security threats. Threats like ransomware, CryptoLocker, CryptoWall and zero-day attacks are continuously evolving. If your organization needs to stay HIPAA- or PCI-compliant, NGFWs provide the extra security measures that help meet those requirements.
There are still many places where traditional firewalls are a good fit. However, it’s important to know that many traditional firewalls are reaching their end of support. If you’re looking for an end-to-end solution, considering an NGFW might be the next logical step for your organization.
Designed for easy deployment and manageability, the Lenovo ThinkAgile SX for Nutanix integrates state-of-the-art Lenovo ThinkAgile HX Series appliances, premier Lenovo networking and management infrastructure into a turnkey, virtualization-ready system. Lenovo ThinkAgile Advantage provides comprehensive life cycle support and end-to-end case management.
Simplify Your IT
The ThinkAgile SXN allows you to centrally manage virtual and physical resource pools, reduce planned and unplanned workload downtime related to physical hosts, and avoid disruption and wasted time.
- Designed for rapid deployment, rack-level scalability, and easy manageability
- Ships fully integrated, tested, and configured for breakthrough time-to-value and reduced business risk.
- As a ready-to-go data center or hybrid cloud infrastructure, enables rapid cloud migration and allows you to deploy your workloads—including back office, Virtual Desktop Infrastructure (VDI), database and analytics—with ease and confidence.
Increase Agility
Designed to interwork seamlessly with your existing infrastructure, to reduce deployment effort, increase your uptime, and save time and money.
- Reduces human errors, increases uptime, and enhances operational efficiency by automating switch configuration in a Nutanix cluster with ThinkAgile Network Orchestrator.
- Industry-unique Lenovo ThinkAgile Network Orchestrator on the Lenovo CNOS switches work with Prism management to automate manual tasks and remove scheduled maintenance windows.
- Accelerates administration and ultimately reduces OPEX, downtime, and errors by:
- Automatically configuring the physical network based on discovered topology
- Detecting changes in the virtual network and dynamically updating the physical network in response to new VMs, updated VMs, and deleted VMs with no user intervention
Faster installation, faster and easier deployment, reduced complexity, and quicker and more dependable support all contribute to a lower cost of ownership.
Experience Data Center Transformation
Easier than ever infrastructure configuration, deployment, and scalability at the rack and multi-rack level.
Deploy workloads in hours—not weeks— with Lenovo’s best-in-class supply chain, plus integration, validation, automation, and configuration at the factory, giving you substantial savings on installation costs.
Onsite deployment and single point of support through ThinkAgile Advantage for full end-to-end life cycle management, facilitating quick problem determination and minimized downtime.
“Pay-as-you-grow” economics enables you to add one or more Lenovo ThinkAgile HX nodes at a time as modular building blocks, to keep pace with your business growth.
Are you looking to boost your business efficiency and agility? Is your data center showing its age, unable to handle current growth rates, and unable to deliver the performance required by applications such as big data, analytics and mobility? Are you looking to reduce the cost and complexity of your IT environment while increasing performance?
Hyper-converged infrastructure (HCI) combines software defined storage, compute and networking functionality into a simple, easy to use appliance. HCI can help you:
- Improve storage utilization
- Provision faster
- Improve staff productivity
- Reduce downtime while improving application availability
- Improve compute utilization
Learn more about Hyperconverged Infrastructure and how it can help your business by reading the IDC infographic below.
View Infographic
Well … it’s been a good run.
Possibly the most widely-used operating system – Windows 7 – is finally being phased out. On January 14, 2020, Extended Support will end for Windows 7 (Service Pack 1). However, another operating system, Windows Server 2008, will precede Windows 7 to the island of misfit software a day earlier, on January 13, 2020.
So, what does this mean? What happens after Extended Support has ended? I’ll break it down for you.
First, we should distinguish between the two main types of support from Microsoft: Mainstream and Extended Support.
Mainstream Support
Mainstream Support is the first phase of the product lifecycle. At the supported service pack level, Mainstream Support for products and services includes:
- Incident support (no-charge incident support, paid incident support, support charged on an hourly basis, and support for warranty claims)
- Security update support
- The ability to request nonsecurity updates
Note: Enrollment in a maintenance program may be required to receive these benefits for certain products.
Both Windows 7 and Server 2008 have been out of Mainstream Support since January 13, 2015.
Extended Support
The Extended Support phase follows Mainstream Support for business, developer, and desktop operating system products. At the supported service pack level, Extended Support includes:
- Paid support
- Security update support at no additional cost
- Nonsecurity-related updates require Extended Hotfix Support to be purchased (per-fix fees also apply)
Extended Hotfix Support is not available for desktop operating system consumer products. More details are available here.
Note: Microsoft will not accept requests for warranty support, design changes, or new features during the Extended Support phase.
- Extended Support is not available for consumer, consumer hardware, or multimedia products.
- Enrollment in a maintenance program may be required to receive these benefits for certain products.
From <https://support.microsoft.com/en-us/help/14085 >
What happens next?
Now that we have that out of the way, allow me to break this down so it’s a little easier to understand.
While Windows 7 is in Mainstream Support, Microsoft will provide full support, updates/patching, and will release quality of life (QOL) improvements such as changes to user interface, performance tweaks, etc. Most Microsoft products stay in Mainstream Support for three to five years.
Once in Extended Support, Microsoft will support your software, but only for a fee. However, even if you are in the Extended Support phase, it does not guarantee you support, as you may have noticed above in the notes, “Enrollment in a maintenance program may be required to receive the benefits for certain products.” Once Extended Support has ended, Microsoft’s solution for any problem regarding these operating systems will essentially be, “upgrade your operating system.” Even if you are willing to pay, these agreements are reserved for large enterprises with thousands of PCs and a large checkbook.
But that’s just the beginning. The need to upgrade isn’t only because Microsoft won’t provide tech/incident support for your operating system, it’s because they won’t patch it either. If you noticed, January 14, 2020, is on a Tuesday. This happens to fall on the infamous Patch Tuesday for that month. Simply, this means that after that date, Windows 7 and Server 2008 will no longer receive security updates and patching, so any security flaws found or left behind on January 13 will not be patched. If you leave these machines on your network, you could be leaving a door open for a slew of cyber threats.
Start planning for upgrades now
So why are we bringing this up now? January 2020 isn’t as far away as you think. Some users may not have any systems with these operating systems, while others may have hundreds. Just like any other business expense, you don’t like the ones that come unexpectedly. The time to start planning and budgeting your upgrades is coming up fast.
When it comes to maintaining a disaster recovery plan for your organization, the 3-2-1 Backup Rule is the gold standard. For many years, we have worked with clients to implement effective disaster recovery plans, and we live by this rule to keep their data protected.
What is the 3-2-1 Backup Rule? Simply put, organizations should make three copies of their data available on two different media, with one stored offsite. While it sounds easy enough, many organizations don’t follow it. Like anything else, you still need to focus on the details to ensure your data can be recovered.
Why isn’t one backup enough?
Imagine that you keep your original data on one device, and its backups are on a second device with the same characteristics, and their failures are statistically independent. For example, if device #1 has a probability of failure that is 1/100 (and the same is true for device #2), then the probability of failure of both devices at the same time is:
1/100 * 1/100 = 1/10,000
This means that if you have your primary data (on device #1) and two backups of it (on devices #2 and #3), and if all devices have the same characteristics and no common failure causes, then the probability of failure of all three devices at the same time is:
1/100 * 1/100 * 1/100 = 1/1,000,000
For this reason, having more copies of your data means you will have less risk of losing data during a disaster. In short, if your data is important to you, be sure to make at least two backup copies.
Use two different media types
Copies of your data should always be on multiple device types. Media storage options include tapes, external hard drives, USB drives, SD cards, CDs, DVDs, or even floppy disks, or on two internal hard disk drives in different storage locations.
Keep one data source offsite
If your office were to be hit with a disaster, like a fire or a tornado, having multiple backups in one location would not do you any good. By keeping the data replicated offsite, you significantly increase your recovery percentage.
If you would like to learn more about how YYTECH can help your organization implement the 3-2-1 Backup Rule, contact us today.
Some information in this article was excerpted from the veeam.com blog.
Meet Lenovo ThinkAgile HX Series
ThinkAgile HX Series integrates Nutanix software onto Lenovo’s highly reliable and scalable servers to dramatically accelerate time-to-value and reduce
infrastructure maintenance time and costs. Get extreme reliability, dependable security, extensive and predictable scalability, simplified management,
and faster time-to-value.
- Simplify IT infrastructure: ThinkAgile HX Series helps break down IT silos to dramatically reduce server, storage and virtualization complexity
in data centers of all sizes.
- Reduce costs and accelerate time-to-value: The flexible building block of fully integrated and tested compute, storage, and preloaded virtualization
management software enables easy scale-out clusters to support your business growth, while reducing your data center footprint.
- Deliver greater reliability: The success of deploying a hyperconverged solution depends on reliable server platforms that play a larger
role. Hyperconverged systems consolidate servers, storage, and virtualization into one virtual structure, easily managed in scale-out clusters
through a single interface.
- 1000 Series is optimized for remote office/branch office (ROBO) deployments.
- 2000 Series is optimized for smaller deployments (small and medium businesses (SMBs))
- 3000 Series is optimized for compute-heavy applications
- 5000 Series is optimized for storage-heavy workloads.
- 7000 Series is optimized for high-performance environments.
If you are interested in learning more about the Lenovo ThinkAgile HX Series, contact YYTECH today.
Have you ever stopped at a gas station and been asked to enter a PIN number or maybe your zip code while paying at the pump? Recently I stopped at a gas station far off the beaten path and, to my delight, was asked to enter both! Being asked for two separate types of information is a form of “Two-Factor” or “Multi-factor” authentication that proves your identity more than one time.
Unfortunately, in our world of cybercrime and digital fraud, our identities and data are on the cybercriminal’s radar 24/7. Fortunately, there are ways to reduce the risk of your personal information being compromised.
Two easy ways to add a layer of security to our identities and data, both personally and professionally, is to practice Two-Factor Authentication (also known as 2FA) and exercise good password hygiene.
What is 2FA? It is an added layer of defense used to protect the security of your accounts beyond a simple username and password. 2FA is commonly derived by picking two of these three options: Something you know (i.e., password), something you have (i.e., smart card) and something you are (i.e., fingerprint). Historically, “know” and “have” have been commonly used requirements; however, biometric continues to increase in popularity. To increase your security, consider adding 2FA to your online accounts and mobile devices.
Use complex passwords that do not contain any easily identifiable personal information such as name variations, family members or identifiable numeric sequences. A commonly acceptable complexity level is to use three of these four character types: upper case letters, lower case letters, numerals, and special characters. As an example: Sp3cialP@ssword! is an acceptable password; SpecialPassword is not.
Also, random passphrases are gaining acceptance. Random passphrases provide an excellent combination of memorability, easy typing, and security. For example: awesome cat office kittendog. Utilizing complex passwords or passphrases should be used in conjunction withchanging them on a regular basis (passwords every 60-90 days and passphrases every 4-6 months) and assigning a unique one to each different account. Consider using a password manager to keep it all straight.
Take steps to safeguard your identity and your online accounts. It is not if you will be targeted, but when. Your security begins with your commitment to these two easy steps.
HCI stands for Hyper-Converged Infrastructure and is an IT framework that combines storage, computing and networking functionality into a single software
solution or appliance. Hyperconverged solutions contain a hypervisor (virtual machine monitor) for virtualized computing, virtualized networking and
software-defined storage functionality.
HCI solutions typically run on standardized hardware assets with the added value being in the software-defined elements managed within the hypervisor. Capacity in an HCI is described as nodes, with multiple nodes being clustered together to create large pools of shared compute and storage resources. Since these storage, compute, and network elements are now all software-defined, virtualized across an underlying pool of hardware, resources management can be facilitated across all instances, and the entire environment becomes simpler to manage via a single interface.

As data volumes increase, response times shorten, and data center infrastructures age, IT managers are most likely evaluating or moving towards Software-Defined Storage (SDS) to get more performance out of the same physical footprint. HCI extends that cost, maintenance and space savings to the whole computing stack by combining compute, network and storage functionality into a single, easy-to-manage appliance.
HCI can lower infrastructure total cost of ownership (TCO) by requiring less hardware, thereby lowering your datacenter footprint, which results in lower power, cooling and maintenance costs. A recent study by Enterprise Strategy Group (ESG) cited a 61% lower datacenter facility cost when using HCI.
HCI can also reduce operational expenses as its modular nature requires less administration, reduces deployment times and simplifies management. The same ESG study from 2016 found that HCI could reduce personnel costs by up to 77% by minimizing the number of silos, people, and hours spent performing routine administration and maintenance tasks. Finally, hyperconverged systems scale seamlessly. Adding capacity is as easy as adding a node, and all nodes are managed via the same single interface.
Hyperconverged infrastructure is the next phase of the evolution of the data center. The hardware-defined systems of the past are showing their age, rigidness and inability to serve the needs of modern consumers. Converged infrastructures have been compressed and their elements have been virtualized and software-defined, removing the silos from IT.
Just as we no longer carry around a phone, camera and GPS separately, but rather carry around a converged device containing software-defined elements within a single form factor, the days of silos within the data center are numbered. HCI can help you meet your IT performance objectives, while decreasing maintenance costs and data center sprawl. With HCI, you can start small with a department-level project and scale rapidly due to the node and cluster nature of virtualization.
With many HCI vendors on the market, making the right decision will take some planning and forethought. It is a good idea to either do an internal audit or consult with a third-party vendor or business partner to help your stakeholders define their needs and priorities. If you are already working with a vendor to help you move further along the software-defined storage value paradigm/scale, it makes sense to start with them. However, beware of vendor lock-in, keep your options open and define project success before implementing aspects of the HCI value proposition.
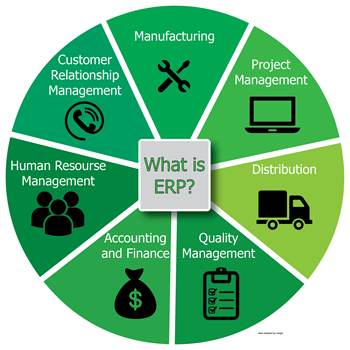
If your business is growing, that’s great news! However, if your growing business is using all-purpose, popular accounting software, such as QuickBooks, there’s a good chance that you will soon need a software that can better manage your growth. This is where Sage 100cloud ERP is a fit. Let’s take a closer look at 8 reasons your business should consider upgrading to Sage 100cloud.
1. Deeper insight for better, faster decision-making: Sage 100cloud features at-a-glance dashboards and has powerful, customizable reporting and analytics that give you the ability to drill down into the details that matter when it comes to managing your business. With this information readily available, you can make faster decisions, stay on budget, and identify new revenue and profit opportunities.
2. Confidence in your accounting: Sage 100cloud is designed to handle the complex accounting needs of growing businesses. By eliminating spreadsheets and other archaic practices, you will have a far more accurate view of your company’s finances, confidence in the face of an audit, and the tools you need to accelerate financial close.
 3. Sage 100cloud leaves room for the future: Your business is growing. Who knows where you could be three, five, or ten years from now? Sage 100cloud can grow with you and easily expands to suit needs as they arise. The modular design of Sage 100cloud allows companies to choose the functionality that best suits their business needs now, and as your needs change, you can quickly add users and modules.
3. Sage 100cloud leaves room for the future: Your business is growing. Who knows where you could be three, five, or ten years from now? Sage 100cloud can grow with you and easily expands to suit needs as they arise. The modular design of Sage 100cloud allows companies to choose the functionality that best suits their business needs now, and as your needs change, you can quickly add users and modules.
4. Simple migration: The switch from your current accounting software to Sage 100cloud will be relatively hassle-free with minimal disruptions.
5. Finally work the way you want to: Sage 100cloud has flexibility that allows user-level Modify/adjust on-site elements to improve relevance and likelihood of ranking for specific terms aligned with the page. and role-based dashboards so you have instant access to the information you want and need to be at your best.
6. It’s easy to use: A larger system means it’s more complex, right? Not when it comes to user experiences. Yes, Sage 100cloud is more complex under the surface to help you manage your more complex business needs, but it is not more complex to use. Unlike other ERP systems, Sage 100cloud has an intuitive, user-centered design so you can focus on your work, not on figuring out the software.
7. Increased visibility and tracking: With Sage 100cloud you will be able to see more than financial information, you can access up-to-the minute information across your organization; from financial to shop-floor and everything in between. You will be able to track inventory in a single or multiple locations.
8. Streamline the back office with integration and automation: Stop wasting time and money on manual data entry and other non-value-added manual processes. Seamless integration between CRM, ecommerce, and financials allows you to eliminate data entry errors and operate an end-to-end business system, automating and integrating everything from accounts receivable management to payroll, sales orders, and everything in between.
If you believe that it may be time to upgrade to Sage 100cloud, our software consultants can explain how these 8 benefits could be a perfect fit for your business, and help you make an informed decision.
Additional Sage 100cloud ERP resources
Business Accounting Software Solutions
The Number 1 Customer-Requested Add-on For Sage 100
In previous versions of Windows, the operating system was serviced with major upgrades (such as Windows 7, Windows 8, and Windows 8.1), service packs, and updates released each month on Patch Tuesday. Windows 10 leverages the “Windows as a Service” (WaaS) model by releasing two types of updates: Feature Updates, sometimes referred to as build updates, and Quality Updates.
Feature Updates are released twice each year and add/update functionality to Windows 10. Feature Updates released recently are Creators Update, Fall Creators Update, and most recently the April 2018 Update. Each build of Windows 10 has a lifecycle of roughly 1.5 years before reaching End of Service.
What this means:
- Microsoft has begun to handle their Feature Updates exclusively.
- IT service providers no longer have the ability to deploy updates from a management service.
- Feature Updates will be automatically installed by Microsoft unless deferred.
- Each Feature Update can be deferred up to 365 days, but cannot be denied. After 365 days from the release, your system will get the update.
Servicing Channels are an option
Don’t lose hope though, there are “Servicing Channels” that you can use to change how Windows 10 is deployed and patched in your environment.
- Semi-annual Channel
- Feature Updates are available once released by Microsoft.
- The standard Servicing Channel can be deferred up to 365 days.
- Long-term Servicing Channel
- Should be used only on specialized devices. Not a recommended option for all machines in an environment.
- POS Systems
- Media Systems
- Medical Equipment
- Feature Updates are not automatically installed and are released every 2-3 years.
- Quality Updates are still available once released to ensure security.
- Does not include Windows 10 Integrated applications such as Edge, Microsoft Store, Cortana, etc.
- Should be used only on specialized devices. Not a recommended option for all machines in an environment.
Quality Updates are monthly updates that roll entire sets of updates into one. In previous versions of Windows, the number of updates each month was overwhelming, and updates could be missed, causing fragmented security on each system. With the Quality Updates, each new month’s update supersedes the previous month and includes all previous Quality Updates. This makes patching more well-rounded and simple.
The Big Picture
Windows 10 is quite different than previous versions of Windows, but Microsoft is set on ensuring security for these systems. Management of devices has been simplified by giving Microsoft more control over which version is installed and supported. Instead of releasing new versions of Windows every three to five years, Microsoft will continue improving Windows 10 with each Feature Update, changing the Operating System gradually as opposed to a sharp contrast seen in version changes such as that of Windows 7 to Windows 8.
There is no anticipated end for Windows 10. Instead of releasing major new versions like Windows XP, Vista, and Windows 7, Windows 10 is just supposed to continually change. If you need assistance with managing updates for Windows in your organization, contact the professionals at Yeo & Yeo Technology.
IT security is a moving target. With cybercriminals using new ransomware and hacking tools to attempt to steal your data every day, security safeguards
need to be in place to stay HIPAA compliant. We have created a safeguards checklist to help your organization stay HIPAA compliant.
When breaking down the technical safeguards for IT security within HIPAA compliance, five standards need to be followed under the Security Rule:
Access Control – The ability or the means necessary to read, write, modify, or communicate data/information or otherwise use any system resource.
Audit Controls – Hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use electronic protected health information (ePHI).
Integrity – The property that data or information have not been altered or destroyed in an unauthorized manner.
Authentication – Procedures to verify that a person or entity seeking access to ePHI is the one claimed.
Transmission Security – Technical security measures to guard against unauthorized access to ePHI that is being transmitted over an electronic communications network.
Each of the five standards have nine sub-standards that also need to be checked off. Some sub-standards are required, while others are suggested:
Access Control – Unique User Identification (required): Assign a unique name and/or number for identifying and tracking user identity.
Access Control – Emergency Access Procedure (required): Establish (and implement as needed) procedures for obtaining necessary ePHI during an emergency.
Access Control – Automatic Logoff (addressable): Implement electronic procedures that terminate an electronic session after a predetermined time of inactivity.
Access Control – Encryption and Decryption (addressable): Implement a mechanism to encrypt and decrypt ePHI.
Audit Controls (required): Implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use ePHI.
Integrity – Mechanism to Authenticate ePHI (addressable): Implement electronic mechanisms to corroborate that ePHI has not been altered or destroyed in an unauthorized manner.
Authentication (required): Implement procedures to verify that a person or entity seeking access to ePHI is the one claimed.
Transmission Security – Integrity Controls (addressable): Implement security measures to ensure that electronically transmitted ePHI is not improperly modified without detection until disposed of.
Transmission Security – Encryption (addressable): Implement a mechanism to encrypt ePHI whenever deemed appropriate.
There are many layers to HIPAA compliance, and various options for managing risk to the security of sensitive health information. If you would like to know more about how Yeo & Yeo Technology can help your business become compliant, contact us today.
Collaboration can make any business better. Nielsen research found that collaboration increases creative output, and that collaborative teams are more likely to identify concepts that will perform well with their target customer group. Beyond just performance, collaboration fosters teamwork and enhances employee morale.
Here are seven technologies that are helping businesses drive collaboration right now.
Video conferencing
Video conferencing has become a go-to collaboration for companies of all sizes. Once limited to boardrooms and large meeting venues, its reach and accessibility have been greatly expanded thanks to the cloud and new PC-based and mobile solutions. Because it replicates nearly all facets of communication, from tone of voice to facial cues, video conferencing solutions inspire the camaraderie and empathy that are critical to collaborative solutions. Besides increasing productivity and fostering stronger, connected relationships among employees, clients, and vendors, video collaboration can also help businesses reduce travel costs.
Interactive white boards
Widely used in academia, interactive whiteboard has been adopted by the business world as a critical collaboration and productivity tool. The No. 1 way interactive whiteboards can improve workflow in business is by increasing engagement in collaborative productions, according to this recent article.
Interactive whiteboards boost communication, make document annotation easier and more effective, and enable a greater range of data sharing and interconnectivity when they include mobile capabilities. Touch-screen whiteboards eliminate the need for a mouse or pointer, making them even more collaborative.
Next-generation projectors
This is a collaborative that has been around for a long time, but the latest generation of projection equipment takes its capabilities to a whole new level. For example, Epson’s BrightLink Pro line combines the qualities traditionally sought in a high-end business projector–brightness, widescreen resolution and split-screen capability– with features and versatility that allow it to function as a multimedia collaborative core in a unified communications solution. It integrates the utility of a whiteboard, projector, and interactive display; easily connects to video conferencing equipment; turns nearly any flat surface into an interactive area where users can annotate; and provides connectivity for mobile devices.
Workspace innovations
Architecture and engineering may be “old school” technologies, but they can have a tremendous impact on driving collaboration when applied to workspaces. Research published in the Harvard Business Review (HBR) concluded that office space is not just an amortized asset but a strategic tool for growth. Much of its value lies in its ability to bust silos by increasing encounters and unplanned interactions–i.e., opportunities for collaboration–between knowledge workers both inside and outside the organization. The HBR article documented increases in productivity, size of business network, and size of social circle among workers using collaborative workspaces such as co-working spaces and huddle rooms.
Social platforms for business
Collaboration has become an essential part of the employee experience, according to the “Forrester Wave: Enterprise Collaboration Report, Q4 2016.” Collaboration apps and platforms allow businesses to share information, locate professionals, coordinate projects, discuss best practices, and build communities within and across the organization. Among the top-rated enterprise social networking platforms for 2017 are Atlassian, HipChat, Asana, Slack, Igloo, Bloomfire, Yammer, and Basecamp. Many of these solutions now incorporate Facebook-like social media aspects, which makes them more attractive to employees, especially millennials.
Machine learning tools
More and more businesses are using machine learning, a form of artificial intelligence, to make their operations faster and more efficient, according to professionals at Accenture, but the same can improve collaboration among workers. Collokia, for example, provides a variety of plug-ins that run in a company’s natural work environment and use machine learning to collect information and map employee skills. It analyzes the collective experience to help eliminate repeated mistakes, accelerate learning, better leverage unknown skills, and automatically connect people with other colleagues, research, solutions, and sources of knowledge.
Crowdsourcing tools
Maximizing positive outcomes from workplace collaboration requires vertical as well as horizontal technologies. Horizontal tools enable peer-to-peer collaboration (among employees or with peers at other organizations), while vertical tools ease collaboration between company leaders and those they manage. Research shows that passion/employee engagement is a key driver of organizational performance, and participation drives engagement. Crowdsourcing tools allow companies to harness the wisdom of the crowd, not just from their own employees, but also from customers, partners, even the public at large. Spigit, a leader in this space, uses analytics and algorithms to help businesses identify their best crowdsourced ideas, assess associated costs and risks, and predict future value. POPin is a tool that helps leaders unite and engage the organization in solving how to achieve strategic goals.
Driving new opportunities
The old saying, “two heads are better than one,” certainly holds up in the digital-driven age. is driving collaboration in ways we could not have imagined a decade ago. Tools we rely on today will likely get even better in the future; and they’re sure to be joined by some entirely new contenders to create unprecedented opportunity for businesses of all sizes.
This content was produced on behalf of Epson by Inc. Studio.
© 2018