5 Cybersecurity Best Practices for Remote Workers
As remote work becomes more common, it’s important to consider the potential security risks that come with it. When employees are working from public places or their own homes, it’s essential to take precautions to protect sensitive data. Here are five habits that remote workers should adopt to stay safe.
- Choose a private work location: While working from a coffee shop or park may be tempting, it’s important to remember that public spaces can make you vulnerable to cyberattacks. Employees should opt for quieter, more private locations to minimize this risk.
- Avoid public Wi-Fi: Public Wi-Fi networks are often less secure and can leave you open to hacking. Instead, use your phone’s hotspot or a VPN for a safer internet connection.
- Invest in security software: Protective software can help safeguard against malware and cyberattacks, making it an important addition to personal and company devices.
- Keep devices updated: Regularly updating software is not only about accessing new features but also about fixing vulnerabilities that could leave your data at risk. This includes laptops, phones, routers, and other IoT devices connected to your network.
- Manage household risks: Employees should be mindful of potential data breaches even within the safety of their own homes. If they share their space with others, parental controls can help prevent accidental access to sensitive information.
By following these habits and taking other necessary security measures, remote workers can safely enjoy the benefits of working from anywhere. If you need help securing your remote setup, don’t hesitate to get in touch.
Information used in this article was provided by our partners at MSP Marketing Edge.
Recent data indicates that obtaining cyber insurance policies is becoming more challenging, and some organizations are reporting that certain circumstances could lead to claim denials.
In today’s world, it seems every organization is either obtaining or seeking cyber insurance as part of their cybersecurity strategy. As insurers continue to gain insights from the claims stemming from their issued policies, new trends are emerging. According to Delinea’s 2023 State of Cyber Insurance report, cyber insurance is creating a gap that may make the case that tighter security controls are a better answer.
Obtaining a policy is not as simple as obtaining car insurance. According to the report:
- 28% of organizations with less than 250 employees who applied were denied coverage
- 63% of larger organizations had to use insurance-provided solutions/appliances
- 67% of organizations say it took four months or longer to obtain a policy
- 69% of organizations have experienced an increase in cyber insurance premiums of 50% to above 100%
However, once organizations obtain a policy, it’s not as easy as filing a claim and getting it covered. The report indicates that 79% of organizations had to place a claim with their cyber insurer, but many of them were denied for several reasons, including:
- Lack of security protocols in place (experienced by 43% of organizations)
- Human error (38%)
- Not following compliance procedures (33%)
- Not reporting to the insurer first (31%)
These issues create a gap between the rising costs of premiums, additional required solutions, and increased denial of claims. Essentially, it means that people are paying more for a service they may not be able to use. It’s also worth noting that despite an increasing need for additional security solutions, people-related mistakes often lead to claim denials.
To address this issue, it’s essential to educate users through new-school security awareness training. Organizations can significantly lower the risk of successful attacks by teaching employees how to interact safely with malicious content in emails and on the web. This, in turn, reduces the likelihood of needing to file an insurance claim.
Information used in this article was provided by our partners at KnowBe4.
Planning for the worst may not be pleasant, but it is crucial when it comes to cybersecurity. With the increasing prevalence of cyberattacks, it is important to prepare for the inevitable rather than hoping it won’t happen. This article provides insight into what constitutes a cybersecurity incident, how to prepare for one, and what to do if you become a victim of an attack.
What is a cybersecurity incident?
A cybersecurity incident occurs when an unauthorized person gains access to your data or systems, typically through the internet. It is a broad concept encompassing many different types of incidents, including cybersecurity breaches, which involve the loss, publication, or lack of access to data or systems. Whenever an attacker encrypts data and prevents access or steals it, it becomes a security breach.
Plan for the unexpected.
It is critical to plan and respond quickly because the actions you take in the immediate aftermath of an incident can significantly impact its severity. Penalties may be imposed, and you may be required to report any breaches to the authorities.
The key to managing unexpected events is to plan thoroughly, regardless of the size of your organization. A well-designed plan will assist you in identifying any deficiencies in your incident-handling capabilities, such as who to contact for assistance or who in your organization is authorized to make critical decisions.
If you’re planning for an incident, there are three important things to consider:
- Record everything required to keep your business running, such as IT systems, services, databases, and people in specific roles. Determine your minimum viable business and list everything you need to be operational. If you can’t access these things for a specific period, such as two weeks, consider alternatives and plan accordingly.
- Compile a list of critical roles, individuals, and supporting companies that can assist you in critical domains such as customer service, legal, communications, IT, and cybersecurity support. Identify the first person to contact in the event of a cybersecurity incident, as well as any additional people who can help. Consider employees, service providers, technical or legal professionals, regulators, or law enforcement agencies.
- Plan for incident roles and responsibilities and be clear on the priorities. Clear roles are essential for staying focused during an incident. Determine who will make decisions during an incident and in what areas. Write everything down and ensure that it is understood by non-technical personnel.
In the event of an incident, it is critical to remain calm, know what to do, and communicate clearly and promptly with clients and stakeholders. It is also a good idea to simulate a situation like this by bringing key personnel together and working through the points outlined in the incident playbook.
Overall, understanding what you have and what could be impacted in the event of a cyber incident is critical. Preparing your organization and creating a plan before anything happens will pay off in the long run.
Information used in this article was provided by our partners at ConnectWise.
According to a study by IBM, 95% of cybersecurity breaches result from human error. To safeguard your business against cyber threats, it is important to prioritize training your employees. In addition to investing in cutting-edge tools, regular cybersecurity training for your team can help them stay up to date on the latest threats and know how to respond in case of an attack. Here are three common cyber threats you and your team should watch out for:
- Admin attack: Cybercriminals often target email addresses like “info@” or “admin@” because they are usually less protected. However, multiple teams may access these accounts, making them vulnerable. To double your security, use multi-factor authentication (MFA), which can be as simple as using a smartphone.
- MFA fatigue attacks: MFA can feel intrusive, and employees may approve requests without scrutiny. Cybercriminals exploit this complacency by sending fake notifications. Encourage your team to verify all MFA requests carefully.
- Phishing bait: Cybercriminals use deceptive emails to mimic trusted sources, making it easy to fall for a phishing scam. Educate your team to closely inspect email addresses and implement a sender policy framework for enhanced protection.
To make training more engaging, try simulated attacks and think of them as an escape room challenge. This approach can help identify vulnerabilities without assigning blame. It’s also important to involve your leadership team, as they should know the response plan in case of a breach.
Remember, training your staff in cybersecurity is not just smart. It’s crucial. If you need help getting started, don’t hesitate to reach out for assistance.
Information used in this article was provided by our partners at MSP Marketing Edge.
Sage100 CRM helps you simplify the sales process, shorten sales cycles and make the most of every sales opportunity. It automates sales tasks, such as creating quotes and orders, forecasting sales, pursuing leads and converting them into opportunities using workflows.
By using Sage100 CRM software, your team can identify the sources of leads, opportunities and closed sales. They can also seek out customer information for upcoming campaigns and launch targeted email marketing campaigns.
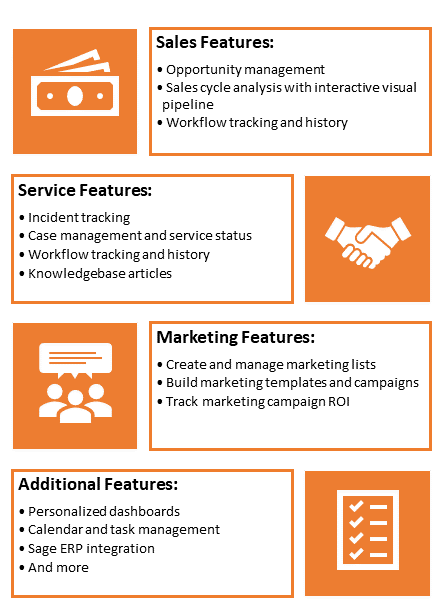 Sage100 CRM integrates seamlessly with Sage100cloud ERP. So, you can track customers through the sales funnel from order to delivery. Sage100 CRM gazes outward at how to better approach prospects and serve customers, while Sage100 cloud ERP gazes inward at how to streamline processes and improve efficiency. Together, these two systems provide a complete solution for your company to increase sales, revenue and productivity.
Sage100 CRM integrates seamlessly with Sage100cloud ERP. So, you can track customers through the sales funnel from order to delivery. Sage100 CRM gazes outward at how to better approach prospects and serve customers, while Sage100 cloud ERP gazes inward at how to streamline processes and improve efficiency. Together, these two systems provide a complete solution for your company to increase sales, revenue and productivity.
Sage100 CRM is also highly customizable. You can choose from fully integrated CRM or Sage Sales, Marketing, and Service modules to suit your business needs.
YYTECH Can Help You Implement a Customized CRM Software.
Find out which CRM software would best fit your organization, contact us today.
Studies show that sitting for extended periods slows your metabolism and raises your risk for obesity, cancer, diabetes, heart disease, and early death. Yet, many employees and students find themselves sitting at their desks for six hours or more every day. Employers and educators need ergonomic spaces that not only decrease health risks, but inspire creativity and collaboration. The solution? Mobile desks.
The Ergotron Mobile Desk allows you to move throughout the office or classroom, adapting to how and where you want to work. Easily go from sitting or standing to collaborate with peers, travel between workspaces or facilitate group projects.
Yeo & Yeo offers Ergotron mobile and height-adjustable desks designed to turn classrooms and offices into active learning and working environments while simultaneously promoting better health.

Studies show that sitting for extended periods slows your metabolism and raises your risk for obesity, cancer, diabetes, heart disease, and early death. Yet, many employees and students find themselves sitting at their desks for six hours or more every day. “We weren’t designed to sit,” said Dr. Joan Vernikos, former director of NASA’s Life Sciences Division and author of Sitting Kills, Moving Heals.
 Kore Wobble Chairs and Stools
Kore Wobble Chairs and Stools
Kore wobble chairs and stools allow for constant movement, decreasing sedentary time and increasing secondary focus. Wobble chairs and stools encourage active sitting, which increases blood flow, activates core muscles, and improves posture.
Other Notable Features
Kore seating products are:
- Manufactured with an FDA approved antimicrobial, which reduces up to 99.9 percent of common bacteria
- Available for all ages from kids to adults
- Made in the USA
- Covered with a lifetime warranty
Learn more about YYTECH’s Ergonomic Solutions on our website or contact us.
How can I tell if my email has been hacked?
The most obvious sign is if you can’t log in. But it’s not always that simple. If you suspect something’s off, check your sent items and login activity for anything that wasn’t you. We can help if you’re worried.
Should I allow BYOD (Bring Your Own Device) in my business?
If managed correctly, it can be an excellent option for some. However, it does pose a serious security risk if you don’t regulate it correctly. Our advice? Seek help to get it set up.
Does my business need cyber insurance?
If you store or send data, it’s a good idea. Every business is vulnerable to an attack or an employee’s error, which puts you at financial risk, so insurance may remove some of the financial burden in such a situation.
Information used in this article was provided by our partners at MSP Marketing Edge.
No matter what kind of business you run, technology sits at the heart of it. And it’s going to become more and more critical in the future. Big thinkers see IT as a long-term investment. They understand the short-term impacts on cash flow and the long-term benefits of business growth, increased productivity and highly satisfied staff and customers.
You’ve heard the saying, “You can’t manage what you can’t measure.” So here are five technology KPIs – Key Performance Indicators – that you could use to ensure you’re getting your return.
- Budgeted IT Spend vs. Actual IT spend: In short, your budget represents the amount you expect to pay, while actuals are the numbers you’ve spent. Having a solid budget in place helps you forecast technology costs and reduce the chances of “urgent, emergency spending.”
- Uptime vs. planned/unexpected downtime: Downtime is when systems and devices are unavailable for your team to do their everyday work. There are two types of downtime – planned and unexpected. It’s crucial to ensure that planned downtime for maintenance has as little impact as possible on your staff and overall productivity.
- Recovery Point Objective and Recovery Time Objective: Recovery Point Objective (RPO) is used to determine how often your data needs to be backed up. This will depend on how often it changes and how critical the information is. Recovery Time Objective (RTO) is the length of downtime your business can tolerate until data recovery. Put another way, it’s how long you realistically have to restore full operations.
- Mean Time Between Failures: Mean Time Between Failures (MTBF) is the average time between system breakdowns. Knowing this can help you measure the performance and reliability of your infrastructure.
- Mean Time To Recovery: Mean Time To Recovery (MTTR) measures the average time it takes your business to recover from a failure: from discovery to fix. This can also be a valuable measure of how robust your business’s infrastructure is, and it can help you decide where to invest long-term.
Of course, there are other KPIs that you could measure to look even more deeply into your IT systems. But these are the ones we recommend starting with. They give you insight into how well your current infrastructure is working for you and help you plan for the future.
Would you like help with determining the right technology KPIs for your business and measuring them? Contact Yeo & Yeo Technology today.
Information used in this article was provided by our partners at MSP Marketing Edge.
How effective is your spreadsheet strategy for fixed asset management? It may appear to get the job done, but the world has shifted to digitalizing all business workstreams for improved efficiency and cost savings. Managing fixed assets is no different.
Fixed asset depreciation, the process of tracking the lifecycles of fixed assets and reporting their value for insurance and tax purposes, is one of the most critical financial processes in any business or organization.
A good fixed asset tracking system is multi-dimensional and more than a spreadsheet can accommodate. And the bigger the organization, the bigger the system requirements.
Six reasons why it’s time to say goodbye to spreadsheets
Here are six common signals it’s time to switch from using spreadsheets to manage your inventory control:
- Missing assets: An incomplete reporting of all assets can lead to tax penalties and insurance issues.
- Lack of privacy and data: Using spreadsheets to manage your fixed assets is a huge security risk. What if someone hacked into your system? Would your data be protected? Using software is a safer route for protecting your assets.
- Trouble with scalability: Tracking a growing capital asset inventory on spreadsheets can lead to data errors and communication breakdowns that negatively impact your business. Your need real-time tracking data to make better decisions.
- You consistently discover errors in your data: Have you found errors in your formulas when calculating depreciation? Entering formulas into spreadsheets often comes with a margin of error since the data is manually entered into the document. Not catching those errors can cost your company money.
Final thoughts
Fixed assets may appear complicated at first glance. After all, they can be subject to many rules, regulations, and depreciation methods and can be physically located in a wide range of geographical locations, making it challenging to keep an eye on.
And that’s before you factor in cumbersome spreadsheets and information silos.
ERP Software can help you better manage these assets, ensuring cost savings for the company and enhanced productivity for everyone involved. With a streamlined process for tracking and depreciation, fixed assets can simply be part and parcel of a well-run organization, enabling its growth rather than hindering its progress.
Want to learn more about our ERP Solutions? Contact Yeo & Yeo Technology.
Information used in this article was provided by our partners at Sage.
In an era dominated by digital landscapes and cyber threats, organizations must remain vigilant in safeguarding their sensitive data and digital assets. Cybersecurity is no longer an option; it’s a necessity. To effectively manage and enhance your organization’s cybersecurity posture, tracking the right Key Performance Indicators (KPIs) is paramount. These metrics provide valuable insights into the effectiveness, efficiency, and resilience of your security measures. Here are some critical cybersecurity metrics your organization should track to stay ahead of potential threats and breaches.
- Mean time to respond (MTTR): This measures the time it takes for your cybersecurity solutions and team to respond after detecting a cybersecurity incident. A low MTTR is critical to reducing the impact of cybersecurity incidents. MTTR can also be broken down by severity or priority.
- Number of false positives: False positives are cybersecurity alerts triggered by benign events rather than actual cybersecurity incidents. Excessive false positives can lead to alert fatigue, decreasing your team’s effectiveness.
- Number of escalations: Escalations occur when an incident is passed from one team or analyst to another for further investigation. A high number of escalations may indicate that your cybersecurity team is understaffed or that analysts need more training.
- Number of incidents resolved: This measures the number of cybersecurity incidents successfully resolved by your cybersecurity systems. It indicates the effectiveness of the systems in protecting the organization from cybersecurity threats.
- Phishing Susceptibility Rate: Tracking the percentage of employees who fall prey to phishing attempts can gauge the effectiveness of your awareness training and the need for ongoing education. A decreasing susceptibility rate indicates improved awareness and resilience against phishing attacks.
Of course, measuring these KPIs is easier said than done. It’s important to remember that cybersecurity includes multiple technical and administrative components working together to maintain the core principles of confidentiality, integrity, and availability. It takes someone with cybersecurity experience to take the important information gleaned from the dashboards and turn it into usable insights.
Information used in this article was provided by our partners at ConnectWise.
According to a recent study, 85% of cyberattacks are caused by human error. Knowing that it’s people causing this significant weakness, it’s the responsibility of organizations to educate and empower their employees to prepare for, recognize, and prevent cyberattacks.
Any robust cybersecurity awareness training program should cover the following:
- Phishing and social engineering
- Access, passwords, and connection
- Device security
- Physical security
Phishing and social engineering
Social engineering is a malicious attack on a user or administrator by deceiving them into divulging information to a bad actor. Phishing is a common social engineering tactic where attackers attempt to get sensitive information like passwords and credit card information by masquerading as a trustworthy source.
Common phishing attempts often require the victim to click on a link, open an attachment, send sensitive information, wire money, or take other actions that leave them and their information vulnerable.
As threat actors continue to create new methods and schemes, their tactics are even more challenging to detect, especially when it looks like it’s coming from a credible source like your CEO or coworker. However, these deceiving attacks often offer a few tell-tale signs, including:
- Content errors. Incorrect spelling, typos, and links containing random numbers and letters are red flags.
- A sense of urgency. An unusual sense of urgency with an immediate request for money or sensitive information indicates the email may be a phishing attack.
- Incorrect emails. An easy giveaway to phishing is when the email sender has a questionable email address. It’s essential to verify the email address before taking any action.
If your people inevitably click on a phishing email, taking immediate action is crucial. Some steps you can take right away are:
- Informing IT and your technology partner as soon as possible. Telling the right person or department is critical in preventing a phishing scam from spreading company-wide.
- Resetting passwords. To avoid additional data loss, change passwords on professional and personal accounts to minimize damage.
Access, passwords, and connection
Generally, users with privileged access perform administrative-level functions or access sensitive data. All employees should know if they’re general or privileged users so they understand what information, applications, or processes are accessible to them.
Similarly, employees should be using best practices regarding the passwords they create, especially those used to access IT environments. In general, secure passwords should:
- Be unique to each app/site
- Have at least eight characters
- Contain letters and special characters
- Stay away from obvious information like names and birthdays
Additionally, passwords should be updated or changed about every six months.
While it may be less obvious, employees should also be wary of network connections outside their homes or workplaces. Even if data on their device is encrypted, it’s not required that a connected network transfers that data in an encrypted format, which opens the door to many different vulnerabilities.
Employees need to be aware of vulnerabilities in public networks and how they could potentially be putting all data exchanged on that network at risk. Encourage end users to use only trusted network connections or a VPN to ensure a secure connection.
Device security
When a mobile or personal device enters the workplace, it connects to the corporate network and accesses all company data. Every device creates more endpoints and opportunities for attackers to capitalize on. Without a secure connection, any mobile device could compromise the corporate network. Therefore, securing these devices is imperative to prevent a business catastrophe.
The same threats to company desktops and laptops also apply to personal mobile devices. Tablets and smartphones may be even less secure because they don’t have pre-installed endpoint protection. To protect the company and its data, users should be mindful of the websites they browse, the apps they install, and the links they click.
Physical security
Unfortunately, digital cyber threats are not the only risks your employees should know about. Physical security also plays a key role in keeping sensitive information protected.
It’s easy to mistakenly leave a mobile device or computer unattended—it happens to all of us. However, if someone swipes an employee’s unattended phone or logs in to their computer, their data will immediately be at risk.
The best way to protect your employees is through awareness. You can increase physical security in and out of the office by:
- Locking up all devices. Get in the habit of doing this every time you leave your desk. For Windows users, press and hold the Windows key, then press the “L” key. For Mac users, press control, shift, and eject (or the power key) simultaneously.
- Locking your documents. Store all your documents in a locked cabinet rather than leaving sensitive information hanging around your desk.
- Discarding information properly. When throwing away or removing documents and files, shred and discard them appropriately.
Build your human firewall with Yeo & Yeo Technology
YYTECH is committed to supporting your organization’s journey to enhance cybersecurity awareness. Our tailored training programs equip your employees with the knowledge and skills to fortify your organization’s security posture. By partnering with YYTECH, you invest in a safer digital future where a well-informed workforce becomes a crucial line of defense. Contact us to learn more.
A lot of businesses are adopting cloud communications to make work more flexible. Before you invest in a cloud solution, it’s worth it to understand what this technology can and cannot do for your business. Here are five cloud communication myths and the facts about how this technology works.
Myth 1: Our Data Will Be Less Secure if We Use Cloud Communications
Security concerns are one of the main reasons organizations hesitate to dive into cloud technology. Data is stored off-premises, which means it’s not just protected by your company. Instead, your cloud provider handles the security for information stored in their data centers.
Using cloud communications tools doesn’t mean your data is less secure. Most cloud providers today are using enterprise-class security protections to counter today’s ever-evolving cybersecurity threats. Also, because their entire business revolves around the cloud, chances are, they are using more advanced security than your business is able to implement with an in-house data center.
Myth 2: With the Cloud, Our Business Loses Control
When your business switches to cloud communications tools, you still retain control over how the software works, who can access it, and what devices your employees use to access it. The software is hosted in the cloud, but that doesn’t mean your administration team can’t manage how the technology is used.
When comparing cloud communications platforms, make sure the one you use has sophisticated administration tools for onboarding and managing users and devices, as well as great customization features. You should also be able to access insights on employee and system quality performance to help your team make well-informed administrator decisions.
Additionally, part of having control is knowing you have a team to help you when you have questions. Make sure the provider you choose prioritizes customer service. You should be able to access technical support and expert help through a chat feature or by phone 24/7.
Myth 3: Getting Started Is Difficult
This is one of the biggest cloud communication myths. One of the reasons for this is the confusion between cloud migration and cloud adoption.
Cloud migration is the process of moving some or all of your workflows and IT systems to the cloud. Because you’re shifting part or all of your infrastructure, cloud migration takes time and requires the help of cloud professionals. It is a difficult and complex process.
Cloud adoption involves adopting one or more cloud services, such as a software-as-a-service solution (SaaS). With SaaS, getting started is simple. You don’t have to worry about business disruption; your employees can start using the software immediately.
Many cloud communications solutions will also integrate with your existing business tools, making it even easier to start leveraging your new software. This is something to look for when comparing cloud-based communication platforms — does the software you’re considering integrate with the specific tools your team is already using?
Myth 4: Cloud Communications Call Quality Can’t Rival That of Traditional Analog Phones
This is a common misconception. This myth exists because many people are familiar with free or low-cost consumer-based VoIP (Voice over Internet Protocol) phone services that deliver less-than-prime call quality. Think of those spotty Skype calls you may have made to friends and family.
When comparing business-grade cloud-based phones vs. analog phone systems, the opposite is true as long as your business has a strong internet connection and enough bandwidth. Your teams will enjoy excellent call quality with a cloud-based phone system, whether they are calling locally or internationally.
Myth 5: Switching to Cloud Communications Will Cost More Than It’s Worth
Not at all. Your business can save time by switching to cloud communications. First, you’ll save on phone costs because you’re no longer paying for multiple business lines, international calls, and maintaining and upgrading communications hardware to operate an on-premises system.
Second, using cloud communications tools makes scaling easier and more affordable. You can add or remove users whenever you need. And, your business can also realize financial benefits because cloud communications are more flexible. You can rely more on working with remote employees, allowing you to save on the costs of providing office space for fully on-premises teams.
Discover How Cloud Communications Can Help Your Business
Whether you’re looking for a cloud-based, all-in-one communications platform, video conferencing software, or a contact center solution, we can help. Reach out to our expert team and find out how cloud communications can help your business thrive.
Information used in this article was provided by our partners at Intermedia.
Of the over 350 brands regularly impersonated in phishing attacks, Microsoft stands out because it provides attackers with one unique advantage over other brands.
The idea behind impersonation is to establish the illusion of legitimacy for a phishing email. This lowers the “defenses” of the email recipient, allowing social engineering tactics to take effect and to get the victim to interact with the email.
According to Abnormal Security’s latest 2023 phishing trending data, Microsoft is the most impersonated brand this year. What’s interesting is that emails impersonating Microsoft only represent about 4.31% of all phishing attacks. This seems low when we’ve covered similar data from Checkpoint, where Microsoft represents 29% of the attacks.
The disparity lies in what the percentages represent. In Abnormal’s case, it’s 4.31% of all phishing attacks (that is, the sum of both those that use impersonation and those that don’t). In contrast, the Checkpoint data represents 29% of all impersonation phishing attacks. While we can’t corroborate the data perfectly, the findings align.
So, why is Microsoft the top brand? Sure, its M365 platform is widely used, but so is UPS or LinkedIn. The reason comes down to what’s of value on the other end of a phishing scam. In Microsoft’s case, it’s credentials.
Credential harvesting is huge with Initial Access Brokers, and a single M365 user credential provides access to a minimum of an email account (for additional BEC attacks) and potentially access to data, applications, and other corporate resources.
So, if your organization is using Microsoft 365, you need to educate users through security awareness training about the dangers of fake Microsoft-branded emails that ask the user to log onto the platform – they are likely phishing scams intent on stealing credentials.
Information used in this article was provided by our partners at KnowBe4.
Do you ever find yourself asking, “What is all this hype about AI?” If so, you’re not alone.
The buzz around artificial intelligence (AI) and its potential to revolutionize every aspect of our lives is inescapable. But how can you navigate through the noise and truly harness the power of AI to meet your business’s goals?
It’s a question that keeps many business leaders awake at night. Here are some of the ways businesses are already using AI.
- Customer service: AI can provide 24/7 assistance, reducing wait times and promptly addressing customer issues. It can simultaneously handle multiple inquiries, freeing customer service representatives for more complex tasks.
- Sales and marketing: AI helps businesses analyze consumer behavior and search patterns, using data from social media platforms and blog posts to help them understand how consumers find their products and services.
- Operational efficiency: With AI, manual tasks can be automated, saving countless hours of input. More importantly, since AI algorithms are designed to be precise, the risk of errors is significantly reduced.
- Enhancing decision making: AI systems can sift through massive amounts of data in seconds, identifying patterns and trends that would take a human hours, if not days, to uncover. AI can delve into levels of data complexity beyond human capacity, unearthing valuable information that might otherwise remain hidden.
- Predictive analysis: AI can analyze historical data to spot patterns and correlations that can forecast future trends and anticipate customer needs.
Imagine being able to predict market trends before they happen or to streamline your operations with almost exact precision. This isn’t some far-off dream; it’s the promise of generative AI. But there’s a lot of speculation around AI. Right now, it’s uncertain, so… should you simply wait and see what happens? Of course not!
In fact, now is exactly the time to start exploring generative AI. Sitting back isn’t an option when your rivals could leverage this technology to gain a competitive edge. Yes, there’s a lot to learn and understand, but isn’t that part of the thrill of doing business in the 21st century?
But one thing to remember amidst the excitement is not to lose sight of your core aims, goals, and culture. What good is a new AI system if it doesn’t align with your business?
While the world of AI may seem like uncharted territory, some classic rules still apply. Will you implement it? Will it generate revenue? Can it reduce your costs? Will it boost productivity? If not, perhaps it’s not the right move for your business.
So, while the hype around AI is deafening, and the path ahead is unclear, the potential rewards are too great to ignore.
As your technology partner, Yeo & Yeo Technology can show you how AI is already helping your business inside applications such as Microsoft 365 and help you talk through how to integrate AI into your future technology strategy. Get in touch.
Information used in this article was provided by our partners at MSP Marketing Edge.
How do I back up my data?
Backing up data can save your business from a catastrophe, so do it! Basic backup can be as simple as connecting an external drive and copying important files. However, you must then remember to do it. The most robust solution is using software that updates all your files securely to the cloud all the time. We can suggest a service if you want.
Our network is slow… can we speed it up?
A slow network is frustrating and can halt productivity. To speed it up, you can upgrade your hardware, optimize router settings, limit bandwidth-hungry apps, and regularly update network drivers. Again… we can help!
Do my staff need USB cameras when working from home?
Most current laptops have great cameras built-in, so probably not. However, the better the image and sound, the better they can communicate. It might be worth investing in cameras, USB microphones, and lighting for staff who speak to clients or prospects on video calls.
Information used in this article was provided by our partners at MSP Marketing Edge.
Hackers are persistent and innovative in the methods they craft to infiltrate corporate systems. Network security acts as your protection against these digital threat actors. The common goal of all types of internet security is to keep cybercriminals out.
Several aspects of your networks require protection, and, as a result, there are different types under the network security umbrella to cover each. Let’s look deeper at the types of network security and what they do.
Access control
Access control protocols use MAC address or IP address signatures to identify devices as they try to gain access to the network. Only devices that are verified and compliant with company standards are granted access. Any unsafe or suspicious device can be quarantined, denied access, or granted limited network access.
Anti-virus/anti-malware
Anti-virus and anti-malware are third-party software apps that protect against viruses or malware. Some viruses and malware can be particularly damaging, so protecting endpoint computers against these malicious files will ultimately strengthen your network security.
Application control
Application control is used to protect mobile and third-party app networks. Whether it’s a third-party application or one you have created internally, apps can be another high-profile target for nefarious actors. This is because open-source code and the virtual containers where some apps are created can be easily infiltrated by malware attacks.
Behavioral analytics
This example of network security involves analyzing the behavior of users and devices on the network. With the help of software tools, MSPs or IT managers can learn to spot trends or suspicious activity over time and catch a potential threat before it starts.
Cloud security
Cloud security uses network security concepts like software-defined networking and software-defined wide area networks (WANs) to protect cloud connections and your most important data in cloud environments.
Data loss prevention
As a strategy, data loss prevention (DLP) is a collection of practices organizations use to prevent the misuse, loss, or unauthorized access of sensitive company data. The technology and tools prevent internal team members from sharing sensitive company data. Your employees constantly upload, download, and share files from various endpoints. By providing them with DLP, they don’t have to worry about those actions causing mission-critical company information to fall into the hands of cybercriminals.
Email security
Email security is a set of practices to protect organizational email networks from hacking. Social engineering attacks like phishing are some of the most popular attack methods hackers use and rely heavily on email. Once employees open a malicious email, click a suspicious link, or download an infected file, the damage is done.
You can rely on some email software to filter out threats and prevent certain types of data sharing, but as emails get increasingly sophisticated and clever, your workforce will be their first line of defense. Train and educate them well.
Firewall
Think of a firewall as the “security guard” or “bouncer” between your network and the rest of the internet. This network filter evaluates outgoing and incoming data traffic against rules and parameters you can pre-set within the platform. Any data packets that violate the rules set within the firewall software are filtered out and denied access to the network, protecting against potential threats. There are also multiple options for firewalls to fit your needs.
Multi-factor authentication
One of the increasingly popular network security examples is multi-factor authentication (MFA). It’s an effective practice and easy to implement for organizations using digital passkey applications or SMS authentication codes. It involves using multiple methods to verify a user’s identity before granting access to the network. Examples are when software applications email or text you a code to enter after entering your login and password, like Google Authenticator.
Network segmentation
Network segmentation partitions a network into smaller segments that are easier to manage (and protect). Overseeing your network in smaller segments affords you greater visibility and more control over incoming and outgoing traffic.
Some industries and organizations may need a slightly different approach to network segmentation. Within the broader discipline of segmentation, there’s a type of network security known as industrial network security. This practice provides the same increased control and visibility to industrial control systems (ICSs). Still, it requires different tactics and tools as these systems tend to be larger and depend heavily on the cloud, making them more vulnerable to cyberattacks.
Sandboxing
Sandboxing creates an isolated environment, separate from the network, where incoming files can be opened and scanned for anything malicious, like viruses or malware. After opening the file in the sandbox, your team or IT partner can evaluate it for any signs of suspicious or dangerous behavior.
Security information and event management (SIEM)
This type of network security uses data logs from any software and hardware within your infrastructure. The SIEM system will review these logs and analyze the data for any signs of suspicious activity. As soon as it detects anything abnormal, the SIEM platform will alert you and your team so you can spring into action—making it one of the most robust cybersecurity risk assessment tools.
Web security
Web security is one of the types of internet security that protects your network from employees’ irresponsible web browsing. Web security applications will block your team members from browsing certain websites based on filters and parameters you can set. Using “web blockers” like this will significantly reduce your susceptibility to web-based threats and sites that may contain malicious files or malware.
Zero trust network access
Zero trust network access is a security framework that grants users only the permissions they need to do their jobs. All other access is denied, creating a much safer environment. The basic philosophy of zero trust network access is a “trust no one” mentality. Anyone who needs access to a certain platform or device within the organization must provide some sort of authorization that they are who they say they are before access is granted.
Choosing the right types of network security for your organization
Setting your organization up with the proper network security types is pivotal to success. Consider the following when choosing network security types:
- What platforms does my organization use the most?
- What are my most important assets (digital and physical)?
- Where is my organization’s most important data stored?
By understanding what platforms and data need protecting, you can build a network security framework that fits your organization’s goals.
Yeo & Yeo Technology can help determine which cybersecurity structure is best for your organization. Contact us today to learn more about safeguarding your network.
Information used in this article was provided by our partners at ConnectWise.
Have you heard of the term “digital transformation”? It’s where you introduce new technology across every part of your business to help you sell more, deliver better customer service, and be more efficient and profitable.
That word ‘transformation’ sounds impressive, doesn’t it? But hold on a minute. Let’s not forget about the most important part of this metamorphosis – your people.
Yes, you read that right. Technology should not be at the heart of any digital transformation … it’s people.
Businesses often make the mistake of getting caught up in the whirlwind of “cool new tech” and forget about the human element. How often have you heard of a company rolling out a major new software system, only for their employees to struggle with the change?
The truth is, the success of any digital transformation hinges on your team’s buy-in. You can have the most cutting-edge technology in the world, but if your people hate using it, it will fail.
So, how do we put people first in digital transformation? It starts with communication. Your team needs to understand why change is happening and how it will benefit them. This isn’t just a one-time announcement but an ongoing two-way conversation.
Next, you need champions. These are individuals at all levels of the business who are enthusiastic about the change and can help others get on board. Enthusiasm is contagious!
And finally, you need to break down silos. The digital world thrives on collaboration, and your business should, too. If departments are working in isolation, you’re not harnessing the full potential of your team or your technology.
Let’s not forget about the role of AI in all this. Generative AI systems, such as ChatGPT, have been making waves in the media, highlighting the importance of the human element in the digital transformation debate. After all, technology should serve people, not the other way around.
The pace of technological advancement is dizzying, no doubt about that. But amidst all the change, one thing remains constant – the importance of putting people, processes, and culture at the center of your digital transformation.
If Yeo & Yeo Technology can help you with any kind of technology project, get in touch.
Information used in this article was provided by our partners at MSP Marketing Edge.
Occupational fraud risk isn’t necessarily shared evenly by all business sectors. Certain industries — for example, construction, real estate, manufacturing and transportation — are usually more vulnerable to employee theft, according to the Association of Certified Fraud Examiners (ACFE). Other industries may not have greater fraud exposure but face specific threats. Here are some industry-related risks and how businesses in these sectors can prevent fraud with strong internal controls.
Construction
Some types of fraud are more prevalent in the construction industry, particularly payroll and billing fraud. Segregation of accounting duties — having them performed by more than one employee — is critical to reducing both types.
To prevent payroll fraud, have someone independent of your accounting department verify the names and pay rates on your payroll. If you don’t already, consider paying employees using direct deposit, rather than with checks or cash. And consider making surprise jobsite visits to compare employee headcounts to time reports and wage payments.
Kickbacks and bid-rigging can be kept to a minimum with extra scrutiny. If your company is suddenly winning bids that it hasn’t in the past and certain bids seem like a stretch, verify that employees have followed your bidding processes.
Restaurants
Successfully combatting restaurant theft generally takes a multipronged approach. If you haven’t already, integrate your accounting, inventory and sales systems. And to manage potential occupational fraud, conduct background checks on new hires, install video surveillance throughout your restaurant and know how to spot red flags. For example, keep your eye on servers who are always flush with cash or purchasing managers with unusually cozy relationships with vendors.
Vendor fraud is particularly common in the food-services industry. It can be hard for managers to keep track of the daily stream of deliveries, which shady vendors might exploit by inflating their bills to reflect more or pricier items than they delivered. If vendors collude with restaurant employees, theft can exact a heavy financial toll. Keep an eye on receiving and accounting employees and investigate any relationships that seem suspicious.
Auto dealerships
If you own or manage an auto dealership, good internal controls generally require your accounting department to post transactions daily. Post new and used vehicle sales, repair orders, invoice payments, payroll and cash receipts.
By 1 p.m. on any given day, you should have access to real-time checkbook balances and other accounting information effective as of 5 p.m. the day before. Timeliness makes it easier for you to spot the first signs of fraud and use the data to catch a perpetrator before he or she gets away with theft.
Medical practices
According to the ACFE, embezzlement — such as stealing cash on hand, forging checks and lying on expense reimbursement requests — is the most common form of occupational fraud in medical practices. As all businesses should, be sure to segregate duties. Avoid having one employee in charge of both approving vendors and purchasing or preparing financial records and reconciling them. If your practice is small, you might want to outsource some accounting activities to help prevent possible fraud.
Conduct background checks when hiring and keep an eye on any workers who seem to be living beyond their means. Employees should know that unannounced audits are possible, but don’t tell them what audits will cover. Also, never let a nonphysician or nonowner employee sign checks.
Customized solutions
In addition to requiring the segregation of accounting duties, certain controls can help any business minimize the risk of fraud. For instance, put a fraud policy in place that spells out prohibited activities and the consequences of committing them, including termination and criminal prosecution. And offer an anonymous hotline that employees, customers and vendors can call to report potential fraud.
For controls that address the greatest fraud threats to your company or industry, contact us. We can conduct a fraud audit to identify potential points of weakness and help you implement stronger protections.
© 2023
It’s official: Windows 10, the operating system that millions of businesses rely on, has been declared “end of life” by Microsoft. Microsoft will soon stop providing technical support, software updates, and security patches for Windows 10. Beyond the end of life date, users of Windows 10 will increasingly face risks of cyberattacks, data loss, and non-compliance with regulations that require up-to-date security features.
But what does end of life mean for your business, and how can you prepare for the transition?
The end of life date for Windows 10 is set for October 14, 2025. While this might seem like a long way off, it is important to start planning for this transition now. Businesses need time to test new systems, train employees, and manage the rollout of a new operating system. Additionally, not all devices running Windows 10 can support Windows 11. Businesses will need time to assess their hardware and, if necessary, budget for replacements.
How to Prepare for the End of Life of Windows 10
- Upgrade to a Supported Operating System: Microsoft has announced Windows 11 as the successor to Windows 10. Businesses should start planning the upgrade process to Windows 11 or any other supported operating system that meets their needs.
- Hardware Assessment: Not all devices running Windows 10 can support Windows 11. It’s crucial to assess your hardware and determine if any upgrades or replacements are necessary.
- Software Compatibility: Not all software that runs on Windows 10 will be compatible with Windows 11. Identify critical applications and check if they will work on Windows 11.
- Data Migration: Important data will need to be backed up and safely migrated to the new system.
- Employee Training: Any change in the operating system will require some adjustments. Plan for training sessions to familiarize your employees with the new OS.
Leveraging IT Support for the Transition
Transitioning to a new operating system can be a complex task. If you have an internal IT team, start planning the transition with them now. If not, consider working with an IT partner who can help assess your current systems, provide new hardware, and migrate your data to Microsoft 11.
While the end of life presents challenges, it also allows businesses to update and upgrade their IT infrastructure. By preparing now, you can ensure a smooth transition to a new operating system when the time comes. For more information on preparing for the end of life of Windows 10 or any other IT-related inquiries, reach out to us at Yeo & Yeo Technology.
Source: https://solinkit.com/preparing-for-windows-10-end-of-life-what-businesses-need-to-know/